
What’s more profitable than ransomware?
Ransomware has been all over the news; everyone is talking about it. Even before WannaCry and Nyetya emerged this year, this type of malware had already made over $1 billion in 2016.
Sounds like a lot of money, but business email compromises (BEC) are 75% more profitable than ransomware. Despite that, they don’t get as much publicity.
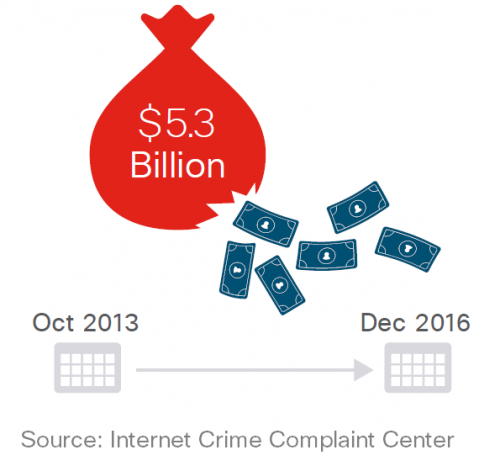
Fraudsters stole US$5.3 billion through BEC between October 2013 and December 2016, an average of US$ 4.7 million a day. In comparison, ransomware made about US$ 2.7 million a day in 2016. The latest Cisco Midyear Cybersecurity Report offers more details on both threats.
What are business email compromises?
BEC are targeted attacks, in which hackers use social engineering to trick people into transferring money to them. There is no malware, no attachments. Unlike ransomware attacks, they don’t take anything from you. It’s all based on lies and misdirection.
Typically, hackers spend some time researching their targeted company and start building a profile. After they know enough, they may send spear phishing emails to senior members of staff, often in the finance department. It needs to be someone with the authority to transfer the money. Of course, the bigger the company, the more money they can make; naturally, larger enterprises are often the targets. However, there’s been an increase in attacks targeting small and medium companies.
Hackers need to achieve two things: establish trust and create a sense of urgency. Both aspects are essential to lead their victims into completing the transaction without second-guessing themselves or verifying the legitimacy of their requests.
For example, the hacker may impersonate a government official via email and pressure your company to pay what is supposed to be a fine, or overdue taxes. They may also take some time to learn more about people in your finance department and use this information to lure them in.
How BEC works
Imagine I am a hacker. I studied your company for a few days and I found out the name of some of your finance directors through LinkedIn. I see one of their posts about a big internal meeting they had last week. I then read in the news section of your website that your company is negotiating a big deal with one of your largest customers. That’s pretty much all I need.
I set up a spoof email account in the name of one of your finance directors, one that looks like a country variation of your main domain (@company.ch, instead of @company.com, for example). I now email one of your finance managers in a different country, introduce myself as a director from another office. To make it sound personal, I even apologise we didn’t have time to meet in person in that big meeting last week. I ask them for urgent help in paying a supplier. I tell them that if the company doesn’t pay by the end of today, we may not close the deal with our biggest customer.
It all sounds legitimate, the finance manager heard my name before, I mentioned the internal meeting, the email account seems genuine and my request is plausible. Before you know it, the finance manager made the payment I requested and only realises the mistake the next day, when it’s too late.
Hackers use a technique called social engineering. It takes advantage of social behaviours, such as curiosity and willingness to help others, to manipulate people into doing what they want them to do.
There are more complex, or simpler variations of BEC frauds. Hackers could pretend to be a vendor and ask for a simple change to their banking details. This way they could receive payments due to legitimate suppliers.
How you can prevent BEC
BEC is hard to prevent because it doesn’t have the most common elements that security tools look for. Make sure you brief your teams on the risks of BEC and establish a checklist for the finance team.
Here are a few things to look out for:
- Don’t rely only on email. Pick up the phone to verify the facts, but don’t use the numbers provided in the emails.
- Set up processes to verify changes in vendors’ banking information.
- Be careful with domains that look similar to your company’s ones. The security department can implement detection systems to flag these domains, but any user can check who owns a domain using websites such as whois.net.
- Set up a rule to flag emails coming from outside your company or from email accounts where the name doesn’t match the reply address.
Stay alert!
Tags:- Access Point
- ACR
- AMP
- annual cybersecurity report
- Artificial Intelligence
- automation
- breach readiness and response
- Business Critical Services
- business email compromises
- CBTC
- Cisco
- Cisco CDA
- Cisco Switzerland
- Citizens
- cloud
- cloud workload protection
- community
- Critical Infrastructure
- cybersecmonth
- data privacy
- data protection
- Datacenter
- Environment
- hybrid-cloud application security
- IoT
- IT Infrastructure
- MCR
- Meraki
- midyear cybersecurity report
- Mobility
- Multi-cloud
- passengers
- ransomware
- Security
- Segmentation
- SmartCity
- social engineering
- sustainability
- swisscda
- Tetration
- Threat Protection
- train
- Transport
- umbrella
- Utilities
- Visible
- Wireless



