
Old School DNS-Based attack to put millions of IoT devices at risk
DNS rebinding has been known and well documented since early 2007, however, with the rise of IoT devices, and mobility it is coming back in a new way impacting countless devices at the internet scale. Devices like, home router Google Home, Chromecast, Roku, Sonos WiFi speakers, and certain smart thermostats could all be interfaced with in some way by an unauthorized remote attacker giving in some case control over the devices.
DNS rebinding allows remote attackers anywhere on the internet to access your home connectivity infrastructure such as your router, hard-drive remote files server, and other IoT devices, by taking advantage of vulnerabilities in how some Internet applications such as web browsers for example cache DNS data and rebind the illegitimate IP to the legitimate associated domain. Therefore once the vulnerabilities is used, internal network resources can be accessed by external servers regardless of firewall settings. Then the C&C server inject malicious code into the browser and can try accessing remote devices such as router by trying default user name and password setting. This can happen because these web browsers acts then as a conduit between the private internal resource and the external malicious server.
How does this attack start?
Like most attacks it starts with an exploit, in most of the case for DNS rebinding it is a phishing attack. The scheme below describe the different phase of how it works. This part only describe the infection phase until it can make the DNS Rebinding request.
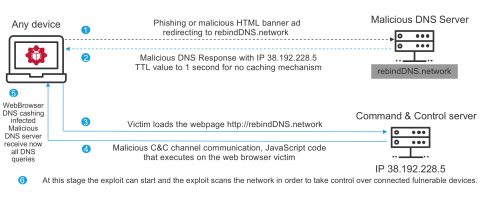
Then the phase in which the web browsers acts then as a conduit between the private internal resource and the external malicious server is not describe here but it is what allows the attack to leverage the infrastructure assets and start taking action then on the remote IoT devices, sending then control and command back to IoT devices rebinding the destination IP with the illegitimate once. The idea afterwards is to gain control to this IoT or network devices using the default configuration setting and take control over them.
How can you protect from DNS rebinding?
First cyber security is always a matter a complacency, so it is important to keep your application and systems up to date, and block risky application such a Java and flash, not that ideally everything should be patch with latest update. Then using solution like Cisco Umbrella formerly Open DNS, you get a global recursive DNS service that allows your DNS request to the outside world to be securely filtered and block the bad DNS or web request resolution. Additional mechanism are offered to protect against DNS rebinding mechanism to the umbrella community as explained below:
- Phishing attack: this is generally where the DNS rebinding starts. Usually this is a fraudulent website that aim to trick the user into handling over personal information or fooling user towards a suspicious destination.
- Newly seen domain: Domains that have become active very recently, this can also prevent new domain when the attacker set up malicious DNS server.
- Malware: This will be capable of preventing the DNS Rebinding attack, it is usually the websites and other server that host malicious software, drive by downloads/exploits. So int he DNS rebinding this could prevent the injection to the browser.
- Command and Control callback: this is also to prevent part of the DNS rebinding. It usually prevents device from communicating with attackers malicious infrastructure.
Umbrella is completely free for home internet security and anyone can start today by simply singing up on the below website. https://www.opendns.com/home-internet-security/
Tags:1 Comments




DNS rebinding allows remote attackers anywhere on the internet to access your home connectivity infrastructure such as your router