
Multi-cloud game: Smarter hackers vs. Stronger applications
When you search the terms: “cloud-native workload protection”, “application workload security”, “hybrid workload protection”, the first that comes in focus is the famous Gartner market statement and definition, backed up by diverse vendor solutions for protecting workloads in the multi-cloud world. I did not (yet) however identify open-source solutions that are associated to the above terms among the scientific community. Can we therefore say that Cloud Workload Protection (CWP) is a new technology? Certainly not per se, but as many other buzz initiatives form the past, it gets clear by now that the current CWP solutions on the market are firmly establishing the cloud security cornerstones in the current technological era.
The expansion of the cloud workload/application protection (CWP) topic has been triggered by the Gartner’s report , the first one appearing in 2016th. CWP addresses the domain of hybrid datacenters (on-premise and in the cloud) and deals with the prime demand for a new security model based on deep visibility into the application’s workloads. As a reminder, the pyramid below, as depicted in the same report, levels up the hierarchy of various security disciplines – from most to least critical, as fundamental methods to workload protection strategy.
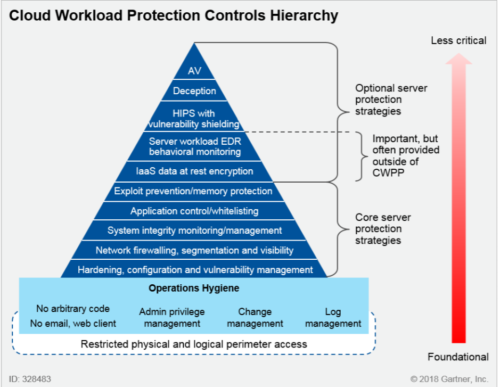
Likewise, several other cloud security studies affirm the undeniable need for transforming the legacy security approaches. The authors of this survey, referring to several analytical sources such as Forbes, point out that cloud-based security is expected to increase up to 42%, by 10% each year. Interesting to note is the discrepancy between the 80% budget spent on cloud solutions vs. 49% businesses delaying the cloud adoption due to the security concerns. While the same research summarizes the vulnerabilities and open issues for cloud-based security, another comprehensive study discusses the requirements for cloud security, pointing out the known threats and attack vectors and offering respective solutions. Going further, some studies are dedicated on providing an assessment methodology for security analysis of cloud-based services.
Another interesting read for me was the “Banking in the cloud: Part 1 – banks’ use of cloud services” – a sequence of articles discussing the drives and the barriers of the major EU banks for adopting the cloud strategy. As an example, security (100%), regulatory restrictions (71%), and public breach notification (43%) (CSA Study) are named as the prominent concerns to the financial sector. These are followed by the loss of control, lack of visibility, auditing and compliance features. All in all, none of the points are attributed to a single challenge, rather to a combination of multiple decision factors. This article clearly captures the “why not” reasons for cloud adoption and confirms the “whys” that are significant for delivering a well-structured CWP plan.
Looking broader let’s try to identify what triggered the idea of such a discipline. Think about the evolution of the datacenter and the way we create networks, services and security policies around them. We witnessed the digitalized era where the application’s infrastructure takes an immense transformational journey. As a reminder, the application’s domain has extended beyond the limits of a single datacenter, embracing multiple interconnected datacenters, to the Edge, and into the public cloud space. We can call this a 1st challenge: heterogenous datacenter networks. The application model undertook changes as well. Supported by the raise of DevOps and automation, building monolithic services shifted to micro-service architectures, containers, dynamic applications, bound to rapid prototyping and releases. Therefore, we can identify the evolution of the applications as a 2nd challenge.
Further in the process, the security model was severely impacted and demanded reshaping. Did the security threats increase, or was it the hackers who gained more skills over time? Both are probably true, but what matters is the outcome of the tight relation between the two – the vulnerability of the complex application world has been responsible for the increase of threats and attack vectors. The multi-cloud evolution didn’t bring-in a custom security model. The legacy approach towards security, as a 3rd challenge, was based on the well-known solutions for threat detection and prevention, that failed short to address the complex applications’ needs and relations. The fixed datacenter security perimeter is an insufficient ultimate solution in securing the evolving applications. And the dynamic (in time and space) behavior coupled with elastic scale (in and out) of applications and containers, did not make the matter easier. The CWP approach brought the attention to the application and shifted the legacy security model away from the network alone. The 4th challenge was to ensure the security model follows the application, regardless of what the application workload does and where it runs.

Shortly, this is how the perspective for workload-centric visibility and protection was established. Workload was defined as a singular task (web server, database, data broker etc.) forming part of a broader application scope that runs specific job on a cloud instance (private or public). With the premise “you can’t protect what you can’t see” the workload visibility aims to show an accurate representation of the application’s behavior and depict an in-depth model of the application’s communication patterns to all the teams in the organization: security, application, cloud, server and networking. What was before considered a task exclusive to the network team, has now became open and visible to a broader group of experts, each capable to drill down into the application and perform certain actions. And those particular actions are what the workload protection covers.
In the next blog, I will talk about the time before cloud workload protection appeared and how this initiative impacts the daily routines of the involved teams. We will see why the traditional security model is out of date and how the new trends are tracing the way towards the development of cloud workload protection platforms.
Tags:


