-

Business-Driven Information Security – part 2
SecurityWhy Security Architecture requires a holistic approach As I said last time, when considering security architecture, many people make the
Read More -

Business-Driven Information Security – Part 1
SecurityWhy you should consider the overall risk – and every permutation of that risk – when developing your security architecture
Read More -

Demystifying SD-WAN Security
SecurityCisco’s distinguished Engineers, Dave Carrel and Brian Weis, recently released an IETF draft RFC titled ‘IPsec Key Exchange using a Controller‘.
Read More -

Let’s fight cybercrime together…
Cisco UKI…with the Cisco NetAcad cybersecurity training. It’s an exciting time in the digital world, and we’re really proud to be
Read More -

-

Meet our man on a cyber mission
SecurityGraham Bartlett, Cisco’s UKI Senior Technical Leader in professional services security, explains why defending our Critical National Infrastructure customers from
Read More -

Watch Ovum reveal the truth about security in digital transformation
SecurityAt Cisco we’re fond of describing cybersecurity as being like the brakes on a car. Brakes aren’t there to make
Read More -

So really, how secure is your collaboration solution? Find out more LIVE with Cisco experts…
CollaborationI had a letter from my bank this week asking me to give them a call about fraudulent activity on
Read More -
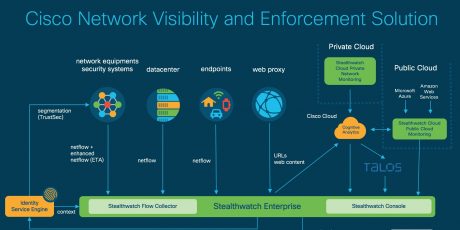
Make Visible The Invisible To Better Protect Your Assets
SecurityFaced with the growing number of new threats, information security managers (CISOs) have no choice but to put in place
Read More -

Protecting Against Supply Chain Attacks.
SecuritySupply chain attacks present a tempting opportunity for threat actors to introduce malicious software into organisations. Compromising the software update
Read More











