
Business-Driven Information Security – part 2
Why Security Architecture requires a holistic approach
As I said last time, when considering security architecture, many people make the mistake of believing that building security into information systems is simply a matter of referring to a checklist of technical and procedural controls and applying the right security measures.
I referred to the SABSA whitepaper Enterprise Security Architecture – A Business-Driven Approach * which uses a chain analogy to explain why security components must be considered together rather than in isolation.
But a chain doesn’t fully depict the nature of security architecture.
Imagine a list containing the components of a car – below are just some:
- engine block
- pistons
- piston rings
- piston rods
- bearings, valves
- cam shaft
- wheels
- chassis
- body
- seats
- steering wheel
- gear box.
If your checklist included every element needed to build a car, does it mean you would have a car?
Not exactly!
Complex systems in action
A car is a good example of a complex system; it contains many sub-systems, which in turn have sub-systems of their own, plus multiple components. Designing and building a car needs a ‘systems-engineering’ approach and resolution to a series of questions that the checklist approach doesn’t address, such as:
- Do you understand the requirements?
- Do you have a design philosophy?
- Do you possess all the necessary components?
- Do these components work together?
- Do they form an integrated system?
- Does the system run smoothly?
- Is the system correctly assembled?
- Is it properly tuned?
- Do you operate the system correctly?
- Do you maintain the system appropriately?
Driven by detail
As well as understanding these layers of complexity and how they need to operate together, the key to developing an effective security architecture is always to think in business terms. Even when you get down to the finer detail – the nuts and bolts, so to speak. And whether you’re a security specialist or customer, avoid making classic mistakes by always asking yourself the following questions:
- Why am I doing this?
- What am I trying to achieve in business terms?
That’s not the end of the story. You also need to persuade all those around you – many of whom may not understand strategic architecture and might think security is simply about technology. A successful Security Architect needs to clearly communicate these concepts, demonstrate their benefits, and help customers do the same within their organisations.
Identify your attributes
SABSA’s Business Attributes-based approach is unique in translating business requirements neatly into a security context. Combining this approach with our best-of-breed security portfolio makes solving real business problems both logical and achievable.
Business attributes profiling for example, populates the missing-link between business requirements and process/technology design. Each attribute is an abstraction of a business requirement (confirmed goals, objectives, drivers, targets, and assets), and can be either tangible or intangible.
This approach in action
An Enterprise Security Architecture model is made up of a series of phases, from we can build a light-touch Risk Model. We take our customers through a journey that explores:
- What their business does
- What assets need protecting
- Why these specific assets need protecting
- What the threats to these assets are.
Enterprise Security Architecture Model
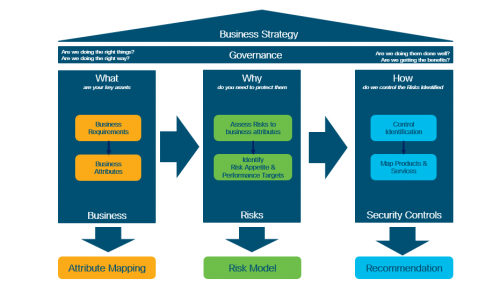
The final phase is choosing the right products and services, in the form of security controls.
More on this next time.
In the meantime for further information about our security products and services, visit our website or contact me.
* Enterprise Security Architecture – A Business-Driven Approach: John Sherwood, Andrew Clark and David Lynas.
Tags:



