The Canadian Bacon: Are your Work-From-Home Users Secure?
Companies everywhere have ramped up their remote access platforms to ensure that work can continue during the pandemic. This focus was necessary, but now we have to wonder: Have we left the door open for the adversary?
Many organizations were not designed to support work from home (WFH) technologies at this scale; nor have they developed the security capabilities required to reduce the overall risk that comes from increased use.
Let’s talk details.
While scaling out your remote access solution you may have needed to do some things that you wouldn’t normally do, such as split-tunnel the traffic to meet the workloads required by your users, expose web-based technologies “as-is” to keep the business operating, and/or allow users to disconnect from VPN and have unfettered access to the internet.
These are just a few examples of threat vectors that could expose your company to risk.
We know that the adversary has seen COVID-19 as an opportunity; and there are myriad real-world examples of phishing, fraud, denial of service, and disinformation campaigns happening as we speak.
With all sports suspended, here’s one for you to focus on. Game on, defenders!

If you have not revisited the access granted through remote work technologies, perhaps now is a great time to ensure that the proper security wrappers are in place so that the organization is not at increased risk.
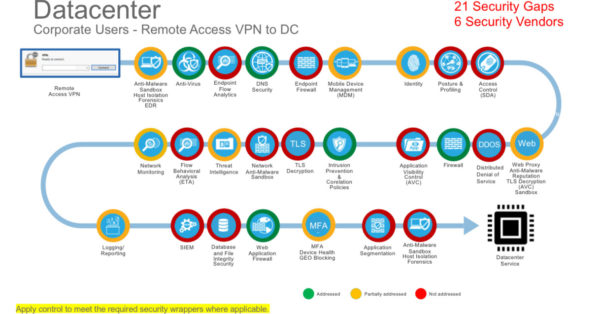
Ideally, you want to step back and analyze your flows to determine the required security mechanisms. I discussed the approach in a previous blog.
Here is an example.
Security tips for the Covid-19 long haul
What can you do to secure your WFH users in the new normal? And how can you do it at scale while not burdening netops/secops teams? Here are some tips.
- Build secure remote access platforms that can scale and are available to meet the existing need; but perhaps also meet the demands of tomorrow (think COVID-19 phase 2). I am seeing many organizations revisit the initial deployment to ensure it can satisfy an increase in demand. What if things don’t change for the rest of 2020 and part of 2021— are you ready?
- Profile your connected devices to ensure they meet security requirements. Consider not only remote access VPN but also web-based technologies leveraging native Transport Layer Security (TLS). We know hackers want to take advantage of assets’ vulnerabilities and once they have access, they may be able to move internally within the network or start screen scraping web-based applications. Now is the time to put additional checks and balances in place.
- Multifactor authentication (MFA) is a must to protect against credential theft and further secure VPN access and applications delivered through native TLS encryption. Credential theft is still a major issue and confidential data could be stolen without anyone being aware.
- Implement endpoint protection (Antivirus or Advanced Malware Protection) and add detection and response capabilities, sandboxing, forensic snapshots, and host isolation. Remember, these assets are remote, so you want to be able to isolate the asset if it is at risk and take a snapshot. Having insight into core applications that are vulnerable is also valuable so you can patch and reduce the overall attack surface.
- Implement DNS layer and web content protection. Remote assets may be connecting to the internet (or split-tunneling) and you want to have an added layer of protection both at the DNS and Web layers; including full proxy with inspection capabilities. Also, forensically you want to be able to centralize all external DNS queries and capture those Uniform Resource Identifiers (URIs).
- Capture the right data to provide insight into applications and network communications. Flow data is not only helpful when threat hunting but can also be used to enhance analytics platforms. Example: Would you treat these differently?
Jason > Windows10 > PowerShell/NT Authority > CNC Server
vs.
Jason > Windows10 > Firefox >CNC Server
- Web-based applications and VPN services as a whole are at risk of denial of service attacks (DDOS). This is even more true today, since the adversary knows that NO service is available if they take down your internet connection. Adding protection to mitigate both volumetric and service impacting events may be the key to ensure your business stays operational.
- Email is still a problem. There has been a rise in COVID-19 attacks trying to take advantage of the user’s emotion. You want to be sure to consider strong email security capabilities that address these attacks as well as typical email threats that exist. Email is still the #1 vector for attacks, so adding layers gives you a much-needed layer of protection.
Now, it may seem like an overwhelming effort to add these security capabilities in a timely manner. However, cloud-based technologies could be the answer. They can remove the need to build supporting infrastructure and reduce the overall time to adopt. In fact, I have seen large companies adopt many of these capabilities in weeks as opposed to months or years, so it is certainly doable.
Finally, make sure you have all of the data readily available for both on- and off-premise assets. Remember, it is not about how many threats you block (although we all strive to achieve 100%) but about handling the breach in a timely manner. Data is key to accelerate this process.
There are many controls and inspection mechanisms in place today such as firewalls that add additional layers of protection (NGFW and NGIPS to name a few). Although I didn’t address them in this blog, these security capabilities are still needed. The tips I’ve provided here are meant to focus on the added threat vector that comes with work from home technologies.
Knowledge is power!
Tags: