
The Canadian Bacon: Security Alert and it’s 5PM on Friday
It’s 5PM on Friday and you are about to pack it in and head out with friends and family for the weekend and it happens. The phone rings and it’s someone from the leadership team asking if you are aware of the latest cyberthreat making its way across the globe. You ask a couple of questions to get some insight, and call your friends and family to let them know it may be a long night! Why? Well, you were tasked with answering the following:
- Do we have protection mechanisms in place?
- Have we been compromised?
So, let’s think about how one does this today with your current security stack. Where does one start in order to answer these questions with confidence? Just think about your current stack – Do you go to your endpoint AV, web content device, next-generation firewall, email security platform, DNS security platform, leverage Netflow, check out your SIEM, etc. to determine whether you have been hit and whether you are protected against the current threat?
Let’s step back and look at an example of what this looks like when leveraging Cisco’s security architecture. The first thing we may need to do is learn a little about the threat and capture the IOCs. Let’s check out Olympic Destroyer (and as we go through this, think about the time it takes you to do the same thing with your current deployment). We analyze the threat using trusted resources such as Cisco Talos, quickly capture the IOC’s and insert them into Cisco’s Threat Response (CTR) tool, and hit investigate.
CTR is a threat hunting tool provided to customers that consume Cisco security technology. CTR is API driven and provides you with investigative and enforcement capabilities from a central platform by integrating the Cisco suite, and adding each as modules (this also allows one to add Virus Total as a source of intelligence). Ok, enough about that. Let’s get back to the problem at hand. Instantly we discover that we have interacted with a known bad hash from a Win7 SP1 box – we can drill into this asset to understand the details such as IP, MAC, Hostname, User, and much more.
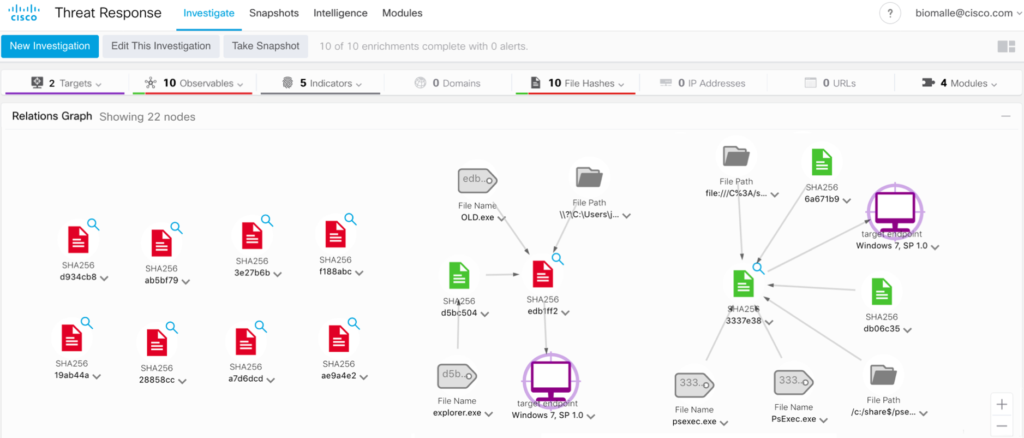
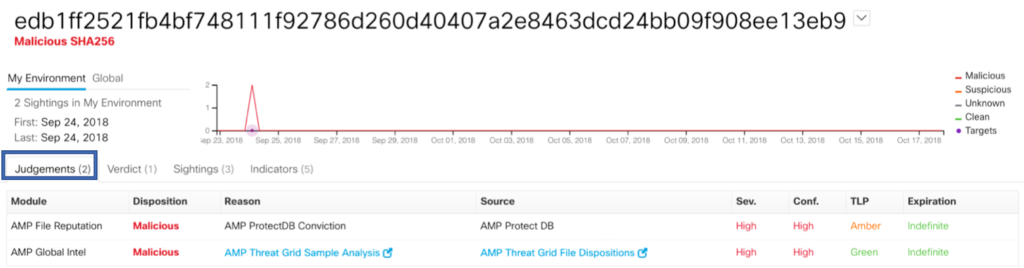
We also can determine whether Cisco is blocking this threat, but let’s analyze this a little further. CTR allows us to get an almost instant centralized view of the IOCs (observations) and the targets within the environment and the relationships between them as seen as above. Let’s focus our efforts on the SHA256 that we know is malicious and one of our hosts was interacting with it. We can look at “Judgements” which provides insight into how/why a file was identified as malicious from all the modules added to CTR. This is where you can also see what database source was aware of the file. This answers the first question – we are protected on the endpoint when leveraging AMP for Endpoints and anything that leverages Cisco’s Malware License (AMP) – this, for example, includes NGFW, Email, and Web – pushing the threat farther away from the asset.
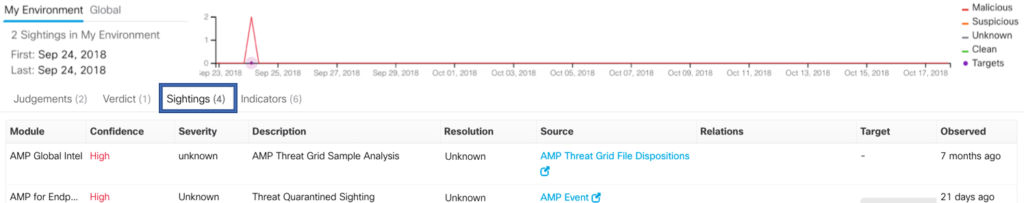
We can also see “Sightings” identifies which module identified the file. Now let’s click on the “AMP Event” which to get more details on what took place.
Clicking the AMP event link brings us instantly into AMP for Endpoints, Cisco’s AV/AMP which also provides endpoint detection and response capabilities. Once inside the AMP for Endpoints console we look at device trajectory that quickly shows us the following:
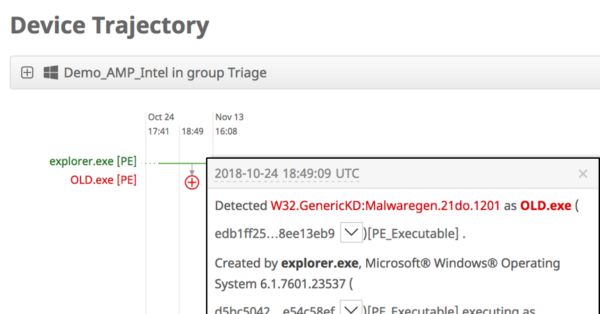
Old.exe was opened by explorer and the file is quarantined. This answers the second question of whether we were exposed. The threat was blocked at the endpoint and no harm was done. The great thing in this scenario was how quick we were able to determine how we were positioned against the threat and the ability to quickly determine that the threat was not realized in our organization. The night is not lost!
An architectural approach to security provides you an incredible advantage. Remember, every vendor is trying to provide 100% security effectiveness but the reality is no one can provide this 100% of the time. The next blog will expand on this discussion with a bit more complexity that requires insight from multiple sources quickly. Now, time to catch up with your family and friends and enjoy your Friday evening!
Tags:


