The Canadian Bacon Series: Securing your Operational Environment
I recently attended the Canadian Manufacturers & Exporters (CME) “Dare to Compete” event in Winnipeg, where like-minded people come together to share their experiences and ideas for the greater good of manufacturing. The event is community-focused, and the goal is to connect with your peers, drive innovation, and compete in today’s global market. The day started off with discussions around company priorities and a need to focus on retaining employees and obtaining new talent. People should be a priority and as we heard at CME, millennials need more than just a paycheck. They need purpose. This is all great stuff, and the discussion was far more than I outlined above, which included multiple breakout sessions with varying topics – all of which provide the industry tremendous value.
What I found interesting is the lack of discussion around cybersecurity. Cybersecurity should be a top priority for any company, including the operational technology (OT) environment. Consider the analogy of what makes a car go fast – you might say it’s the engine, the driver, the fuel – all of which play a role, but none of this would be possible without the brakes. Why? Well without brakes you would only go fast once. The car and driver would not survive – game over.
Cybersecurity is the brakes for your business. It allows you to be agile, go to market faster, and be a differentiator in today’s world where striving to be secure becomes the advantage.
While at CME, I presented with Westburne’s Neal Pinto about securing the operational environment. Discussion attendance was average, and the group was eager to learn, but I observed that representation from both IT and OT teams could have been better. This highlights to me that we have a long way to go when it comes to securing the operational environment. Cybersecurity should be considered a competitive advantage.
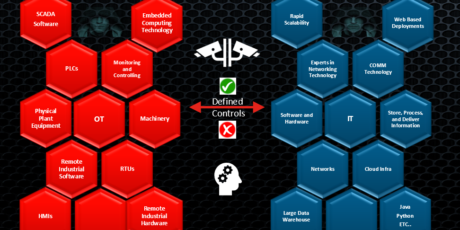
But how do we mature the operational environment when it comes to security? We need to ask our IT and OT teams for the answer to that question. Whatever your role, you should ask or challenge both the operational and informational technology teams on what your security posture looks like in both environments. Note: most cybersecurity risks to the operational environment come from an IT-based system perspective. Having IT-based knowledge provides an advantage, so it’s important for these teams to come together for two reasons:
- Operational teams can educate informational teams about how the operations environment works, and the risks associated with it.
- Informational teams can educate operational teams around managing devices, keeping them updated, ensuring visibility, and control.
What are some of the things you should consider when securing the operational environment? Let’s break it down:
Phase One
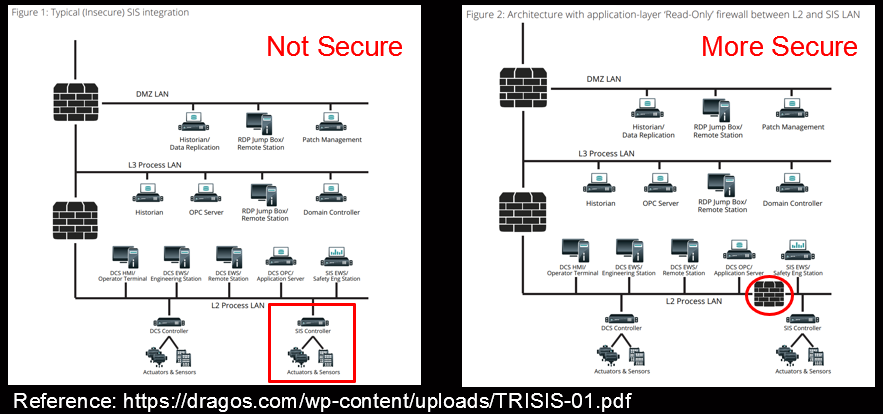
- Put control points in place – This would include boundaries with L3/L4 control. First and foremost, control between the business (IT) and operational environment then extend this where appropriate.
- Segment your network(s) – this includes managed switches and VLANS separating, for example, Safety Instrumented Systems from Control environments.
Phase Two
- Advanced inspection – this may include IDS/IPS, Advanced Malware Protection, and/or Application control. Consideration needs to be made around whether one alert vs. taking action such as a block is right for your business – this is where Operational teams provide much needed insight.
Phase Three
- Visibility – know the environment leveraging flow – this is to your advantage. The operational environment is static in comparison to the business network (IT). Identify the devices operating within the environment.
- Policy Driven Response – the ability to empower OT teams to drive intent and having policy driven controls to allow the intent minimizing cybersecurity risk and operational impact.
Note: there are lots of other items such as supply chain, remote access, cloud, and multifactor authentication, to name a few, to consider when evaluating your operational environment’s security posture. If you’d like to know more about these, leave a comment below.
Security is tough business, but so are Canadians. So let’s ensure that, regardless of the technologies leveraged, we are all asking the right questions, moving the ball forward, and leading the industry together.
Tags:


