
Faced with the growing number of new threats, information security managers (CISOs) have no choice but to put in place solutions to actively manage system and network access, and especially to rapidly detect suspicious or abnormal system activity. Recent attacks have made it clear that relying on perimeter security systems is no longer sufficient to protect companies’ information systems no matter their size.
In recent years, Cisco has developed a security solution that takes advantage of the network infrastructure to detect and respond to abnormal and malicious behavior in real time. This abnormal behavior be the spread of malicious software (malware, ransomware), the exfiltration of sensitive data to a partner’s network, or worse to unknown external systems.
This solution, called Cisco Network Visibility and Enforcement (NVE), is based on a set of technological platforms able to collect a very large volume of metadata from the network, and process and analyze this information as it is generated. This metadata is then correlated with other sources of information such as Cisco Talos to help cyber security operation centers (SOC) to detect and neutralize new threats faster and more effectively.
The success of this solution is based on the ability of Cisco to manage and interface with all kinds of network infrastructure without the need to deploy additional equipment that could weaken or complicate the network. The effectiveness relies on the sophisticated mathematical models (algorithms) developed by Cisco researchers to detect threats, applying the latest developments in artificial intelligence (AI) and machine learning.
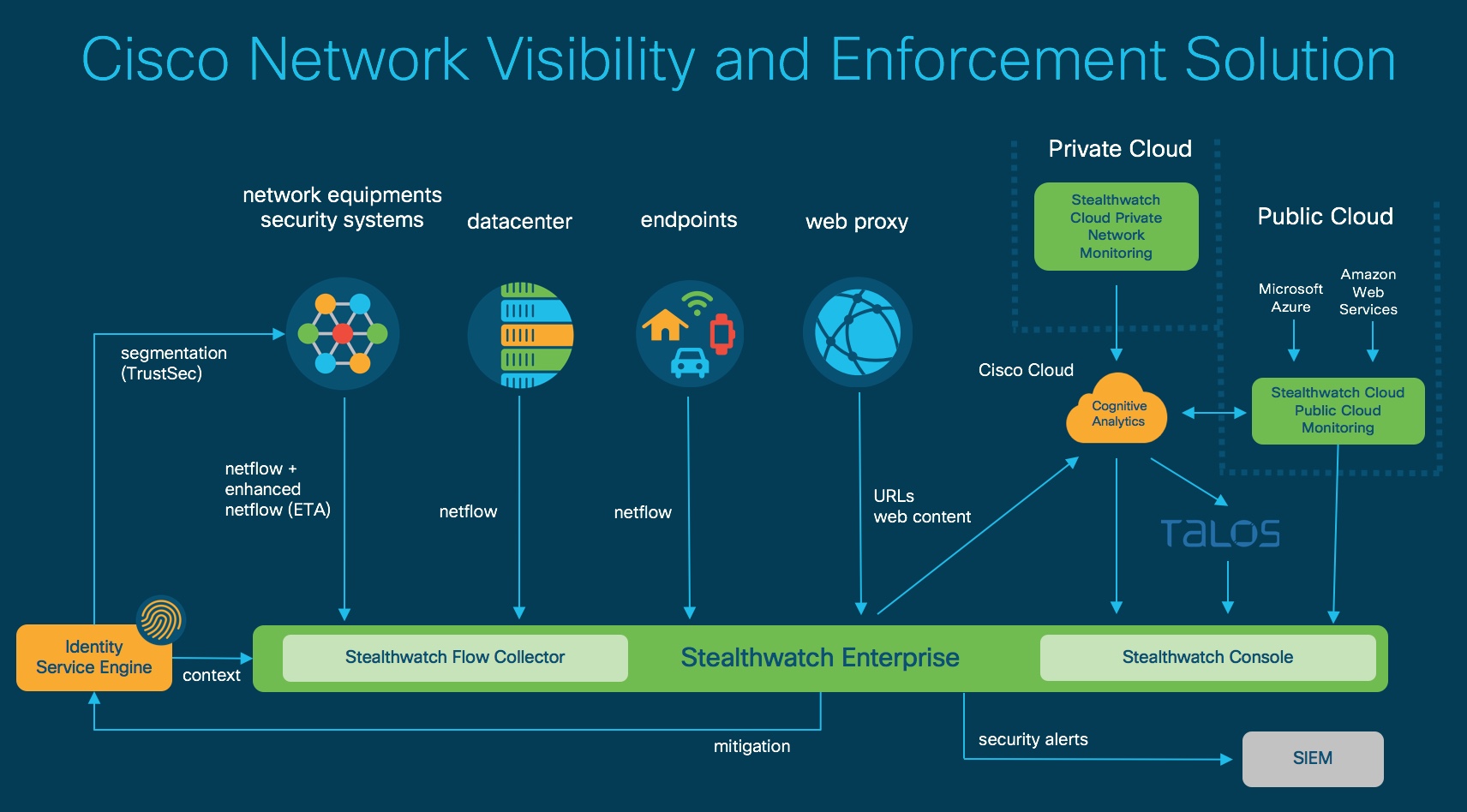
In addition, the NVE solution allows once the threat has been detected and identified to quarantine the infested equipment in order to prevent the malware from continuing to spread or harm the information system by continuing to access to areas of the network to which the equipment previously had access before being infected.
Recently, Cisco has introduced the Encrypted Traffic Analysis (ETA) feature into its network equipment. When ETA is combined with the NVE solution, it detects the presence of threats in encrypted traffic by identifying malicious behavior without the need to decrypt the packets.
With its “The Network Intuitive” initiative, Cisco believes that the protection of information systems in the digital age can only be effective if we are able to monitor 100 percent of network traffic. This encourages companies to deploy systems capable of processing the necessary volumes of data and to extract the essential and useful information in order to better serve increasingly constrained IT teams.
Find out how your network can help you better protect against new threats with the Cisco NVE solution and request a free network visibility assessment.
