The healthcare industry faces unique challenges when it comes to the identification, classification, and authentication of medical devices. Rigid guidelines prevent tampering with or modifying the hardware and software on these devices without a formal submission. With a primary focus on clinical function over security, manufacturers have failed to implement the most rudimentary forms of protection. Features that are often missing include operating system hardening, patch updates, and client security services like personal firewall, anti-malware, host intrusion prevention, or authentication services like an 802.1X supplicant. It can be a time-consuming and costly process to validate compliance after a modification. Consequently, these devices are often deployed in an unprotected state, and manufacturers have little incentive to provide security updates as new vulnerabilities are discovered.
It is common to see medical devices that have been in operation for many years without any modifications that improve or address their security posture. These are the same devices responsible for the safety and health of the patients they serve. Their compromise or failure can result in a failure of the treatment or even death. However, awareness of the security gaps and risks in the healthcare environment has risen significantly. In the past couple of years individual testers have exposed the ease with which medical devices can be compromised or whose functions can be controlled without being detected, even devices that deliver critical care.
Secure access to healthcare networks comprises many topics and technologies.
This blog is focused on three specific topics:
- Secure onboarding of users and devices with Cisco Software-Defined Access
- Segmentation & Access Control with Cisco Software-Defined Access
- Identity-based Policy – Decoupled from VLAN and IP Address
Secure onboarding of users and devices with Cisco Software-Defined Access
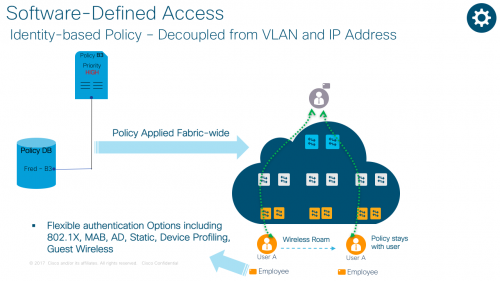
 As networks get more complex, it is taking longer to get people on to the right network with right credentials. Today, we live in a CLI-driven world that allows us to define consistent policy, but just once.
As networks get more complex, it is taking longer to get people on to the right network with right credentials. Today, we live in a CLI-driven world that allows us to define consistent policy, but just once.
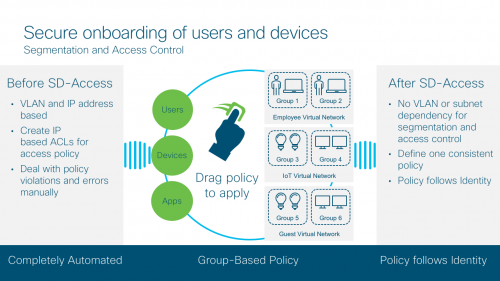
With Software Defined Access, also referred to as Cisco’s SD-Access solution, you can associate a policy to the specific groups with no dependency on VLANs and IP addresses. You can also define one consistent policy, and that policy follows the user from the edge to the cloud. Better yet, you don’t have to deal with policy violations and errors manually.
Segmentation & Access Control with Cisco Software-Defined Access
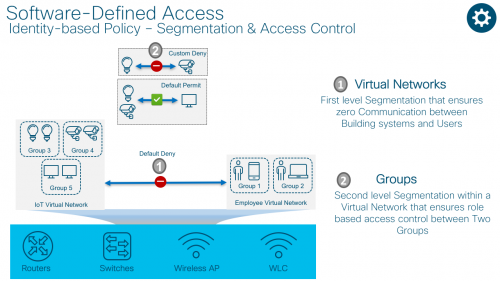
Cisco’s SD-Access solution uses virtual routing and forwarding (VRF) technology as a first level of segmentation which ensures zero communication between two or more virtual networks.
Cisco TrustSecTM is used as a second level of segmentation within a virtual network which ensures role based access control between two groups. This segmentation uses logical tags known as scaleable group tags or SGTs.
Identity-based Policy – Decoupled from VLAN and IP Address
At the point of network authorization, Cisco ISE can “mark” or tag matching endpoints as critical medical devices without changing its VLAN or assigning a specific IP address. SGTs can be used purely for visibility or policy enforcement anywhere in the network. Even Firewalls that support Cisco TrustSec technology can dynamically apply policy without concern over source IP or VLAN assignment, which simplifies rule management.
In the context of medical devices, SGTs offer an attractive option. You can use them to track and monitor medical devices without applying enforcement and later apply more restrictive segmentation and access to and from these devices.
Classification of Healthcare-Specific Devices
In the absence of explicit identity credentials for network authentication, IT administrators must often resort to using the MAC address as the primary method to detect and classify medical endpoints. Some healthcare providers already have an external inventory of their medical devices. If these external databases support direct integration with Cisco Identity Services Engine (Cisco ISE), then lookups to authorized endpoints can be simplified.
Unfortunately, most healthcare providers lack a complete or updated database of their medical devices, including individual MAC addresses. Fortunately, there is still a way to dynamically populate the endpoint database and assign classifications and policies, namely, profiling.
What Is Profiling?
Profiling in Cisco ISE is the automated process of device discovery and classification. It is based on the use of collectors, called probes, as well as on other sources of endpoint context. Probes use specific methods and protocols to collect attributes about each endpoint. The specific information a probe collects depends on the protocol and method implemented.
Cisco ISE supports various probes, each capable of capturing different endpoint data. Raw data for a given endpoint is parsed and stored in the ISE internal endpoint database. Relevant endpoint attributes are then analyzed against a library of fingerprinting rules known as Profiler policies. Different attributes and rules can have different weighting factors in the final endpoint classification depending on the reliability of the data.
Looking for more information?
In my last blog I’ve covered how a single fabric for wired & wireless with host mobility helps to solve challenges in healthcare and in the next part of this blog I will cover how analytics and insights helps.