
As security practitioners we pride ourselves on our ability to respond quickly to remediate threats and minimize the impact they have on our business. We all know at some point a breach will happen. But the constant challenge of tight budgets, fragmented security technologies, and lack of automation doesn’t make the job any easier for Canadian security professionals.
Imagine leveraging many technologies and batting down thousands of threats a day at superhuman speed, but at the end of the day … nobody really cares. I mean, you care, the geek in me cares, and your direct leaders may care. But the business looks at this as your job. No Superhero status for you. What the business will care about is how you handle a breach when it is discovered.
At some point the compromise will take place, and that is when things really matter. You are only as effective as your security capabilities and you need to be ready to respond with technologies that can quickly detect, contain, and remediate threats that elude frontline defenses.
Cisco security solutions are some of the best in the industry and, to make what we build even better, our enterprise agreements give you greater discounts the more security technologies you deploy. Great! There is value in that alone, but I am a geek and what intrigues me more is that we can create security architectures today that we could only dream of in that past.
But let’s take a step back. The traditional approach has been to bolt-on the latest threat protection product in the hope that adding to the patchwork of security solutions does the trick. No more. You need the ability to create a supported security architecture that covers your endpoints, network, and cloud with the ability to share intelligence across the technologies defending your environment. Building this cohesive solution is no easy task, but between vulnerable and secure, there’s a bridge.
Consider this: an employee is connecting to your company’s network. What does their day look like when they use Cisco security solutions? …
The employee connects to the network and is required to authenticate and meet a minimum posture. Once authorized, the employee is allowed controlled access to the network. This capability is provided by Cisco Identity Services Engine (ISE).
The user plugs in their USB key (which is allowed, in this case) and opens a PDF. Let’s assume the PDF is not known to be bad and let’s assume we did not sandbox it.
The PDF then creates a connection to a known CNC. Cisco’s Firepower Threat Defense (FTD) sees the connection attempt and blocks it. FTD then tells ISE about this connection attempt and, based on policy, quarantines the asset.
Additional analysis is performed by your company’s security team and let’s assume they submit the sample to Cisco Threatgrid for analysis. The sample comes back as malicious. A retrospective event takes place and quarantines the file on the endpoint using Cisco Advanced Malware Protection (AMP) for Endpoints.
The malicious PDF is also blocked by Firepower Threat Defense, Email Security, Web Security, and Cisco Umbrella. The goal is to move prevention as far away from the asset as possible and protect all assets, both on and off premise.
The asset is then moved back onto the network. (note: if the team required, they could do additional analysis determining what took place on the endpoint by leveraging Cisco AMP for Endpoint’s Endpoint Detection and Response capabilities.)
The employee then connects to Office 365 which is leveraging multi-factor authentication using Cisco DUO (it is also restricted based on device and GEO). They create an email. It turns out the email’s contents fall under PIPEDA and Cisco Cloudlock restricts the data being sent. It also creates an alert.
The user then receives an email with a malicious link which is removed by Cisco Email Security. If the link did make its way in, by the way, then Cisco Umbrella or Cisco Web Security has another chance to block the connection. Layers that matter!
Finally, a printer starts to communicate in a manner that is different than it should, probing port TCP/445. Cisco Stealthwatch sees the behavior and creates an alert. Your security analyst then determines the asset needs to be moved into a forensic VLAN as it was compromised. The analyst, with a push of a button within Stealthwatch, tells ISE to take action against the hostile asset. Boom!
The only way to win your battles and keep your assets, people, and process safe is to empower analysts with meaningful data, leverage tight integration, and support automation. As you can see in the video below, our security portfolio works together so you can stay safer, respond faster, and deliver automation – so IT resources can go further.
https://www.youtube.com/watch?v=i6GNTwPpZLo
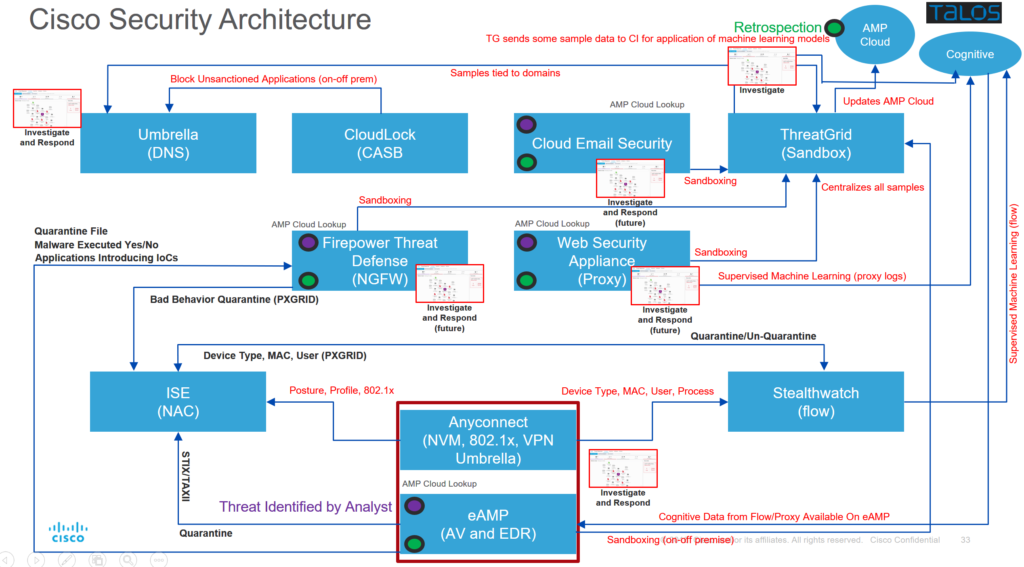
This is just a small example of the possibilities that exist today with Cisco Security. Check out the following video that highlights the Cisco Security architecture in action!
To learn more about Cisco, visit our website.
