Recently, I have been exploring the Pyramid of Pain, a concept that was first introduced in 2013 by cybersecurity expert David J Bianco. The “pain” in his concept refers to the difficulty faced by the adversary in succeeding if they are denied certain indicators.
Pretty cool stuff!
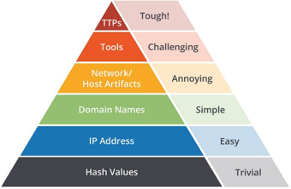
As the graphic indicates, it is trivial for the adversary to manipulate a hash value to bypass a detection engine that matches based on hash. However, adding controls that restrict tactics, techniques, and procedures (TTPs) makes it very tough for them to overcome. I am a big believer in adding as many of these controls as possible; thus, adding a multiplier effect for each defensive capability.
Below is the breakdown of each indicator:
Hash Values (TRIVIAL): SHA1, MD5, SHA256 or other similar hashes that identify a suspicious or malicious file. It is trivial for the adversary to change the value of the hash bypassing the defensive capability: For example, polymorphic or metamorphic techniques.
IP Addresses (EASY): IP addresses are used as an identifier and can be easily hidden by using an anonymous proxy service (like Tor) or they can be changed at high frequency such as leveraging fast flux.
Domain Names (SIMPLE): Domain names (e.g., “internetbadguys.com”) and/or or sub domain (e.g., “exploitkit.internetbadguys.com”). These domains are registered and hosted and can be part of the adversary’s attack infrastructure. The attackers can simply bypass these controls using techniques such as DGAs (Domain Generated Algorithms).
Network Artifacts (ANNOYING): This refers to the ability to determine suspicious or malicious activity from legitimate activity. It goes beyond a user device and includes all Internet of Things (IoT) devices. Examples may include patterns based on network activity (C2 information), Uniform Resource Identifier (URI) patterns, certificates of use, and so on.
Host Artifacts (ANNOYING): This may include an artifact in the registry, a scheduled task, or files dropped within the file system that indicates the presence of malicious activity.
Tools (CHALLENGING): This would typically be software that the adversary brings with them to perform a variety of activities such as creating backdoors for a C2 channel, network sniffers, and password crackers.
Tactics, Techniques and Procedures – TTPs (TOUGH): The tactic provides the description of the behavior, the technique provides more details of the behavior from the perspective of the tactic, and the procedure would provide deep details around the technique itself. Example: The Tactic is “Discovery” and technique being used is “Network Service Scanning.”
Mapping Cisco Security to the Pyramid of Pain
With a better understanding of the Pyramid of Pain and each indicator, I decided to build out a mapping document to highlight how Cisco Security technologies can be leveraged to detect and/or prevent each indicator in the Pyramid of Pain. Cisco Security technologies may also be used during threat hunting/ incident response exercises, providing insight into each attack indicator.
The goal of this mapping exercise is to empower teams with additional insight into where they may be able to investigate indicators and use the knowledge gained to build defensive capabilities throughout the entire security solution stack.
Check out the video series on the Pyramid of Pain and how Cisco Security technologies map to each indicator from a detection and/or prevention perspective.
Knowledge is power!