
The same old approach to security focuses on adding point-products to the solution stack in hopes to gain additional security effectiveness. This approach has been taken by many companies for many years and the results have proven themselves time and time again; more point products plus fragmentation within the stack equals a minimal increase in security effectiveness with an overburden of complexity resulting in the same old approach and continued compromise. Don’t believe me? Just look back over the past 5 years. Can we do better than taking the same old approach to security over and over again? You bet!
We can take a step back and look at this holistically and go beyond the point product discussion. Let’s say you have a project to replace an aging 1st generation Next-Generation Firewall – NGFW (Note: I really hate the term next generation because the label never expires – it’s like buying next-generation bread with no expiration date – yuck!). The need is to replace aging technology, but taking a step back can allow one to take a strategic approach starting with the NGFW replacement (this is an example – this could be endpoint, cloud security initiative, etc.). Of course, you need to evaluate the needs of the point product, but expanding the conversation to further understand the security needs of the business flows you are protecting is key. Going beyond the point product is tremendously valuable and part of an overall security strategy focused on architecture.
This is where Cisco SAFE comes into play providing deep understanding into what is truly required to secure business flows. SAFE focuses on Places in the Network (PINs) which further defines the security elements to secure a flow and it is technology agnostic (that’s right we are not talking about product here). This provides a deep understanding of what technologies are required to ensure business flows are secured which further enables the business to be agile and moves towards secured digitization.
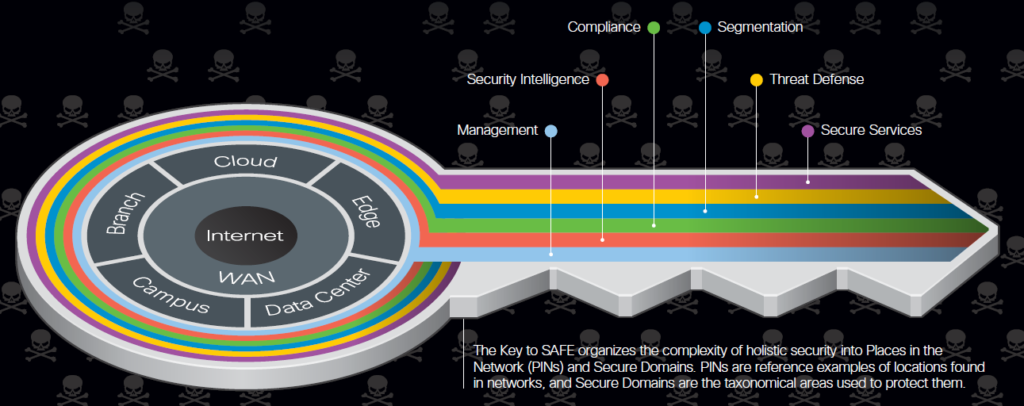
What does a SAFE session look like? It consists of a FREE half-day workshop with a Cisco Cybersecurity expert and your team which includes folks from the business, informational and operational teams, procurement and anyone else that can add context and value (note: some sessions have fewer people and others have more it depends on the organization). During the session, we will capture the executive drivers and initiatives, threats and risks to the business, discover current technologies in use, the number of vendors being leveraged, and finally the gaps associated with the current solution. We then highlight the use cases (flows) that are core to the business and start plotting out what you have and where the gaps are within the current solution set exist. This part of the process is very interactive from both Cisco and the customer as we tackle each flow as an auditor or hacker to determine whether it holds up and is secure. This becomes a blueprint for the organization from a security strategy perspective. A storyboard if you will of what is required to secure each use case. This is more compelling than saying you need a NGFW or an endpoint security product and sharing a bill of materials with leadership.
Let me walk you through a use case: First, we define Places In the Network (PINs).
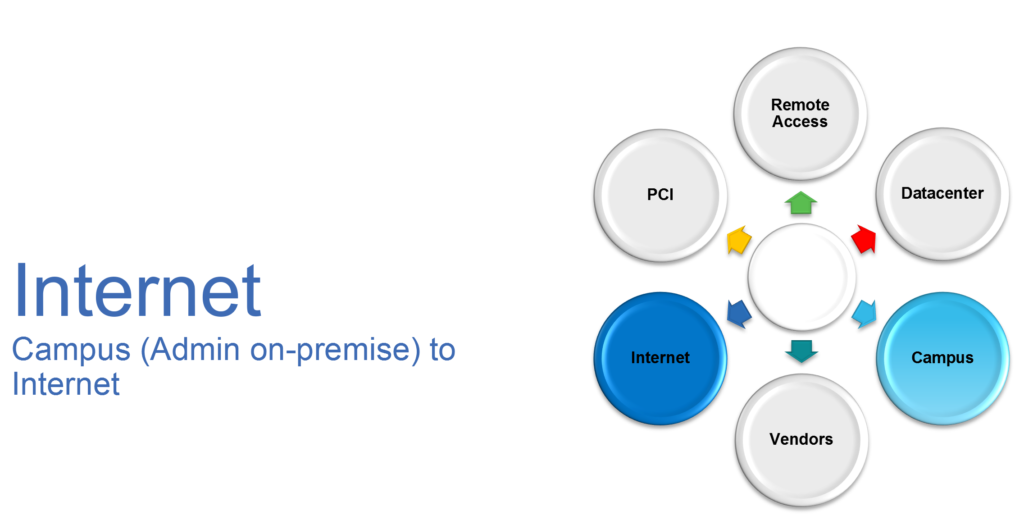
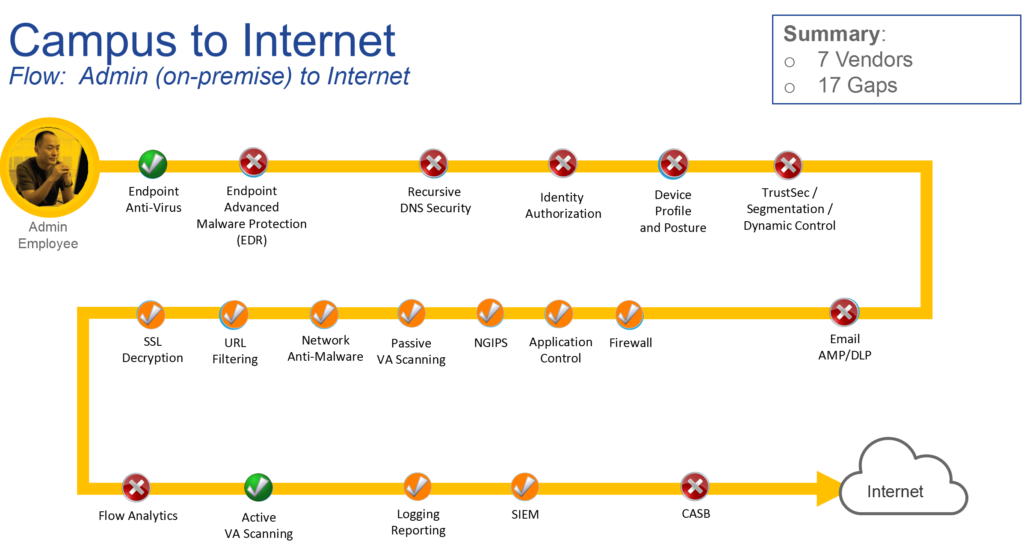
Next, we define the use case focused from PINs and in our case, it is Campus to the Internet: In this use case, we look at Administrative Staff accessing the Internet. Please note that the same administrative staff accessing the internet from outside may have different security requirements or the same user accessing the data center. Each of these would be separate flows.
Through interactive whiteboard discussions, the customer determines that the following is required to secure this flow. (again, think like a hacker or auditor). The below image is an example of the output the customer would receive in the form of a report.
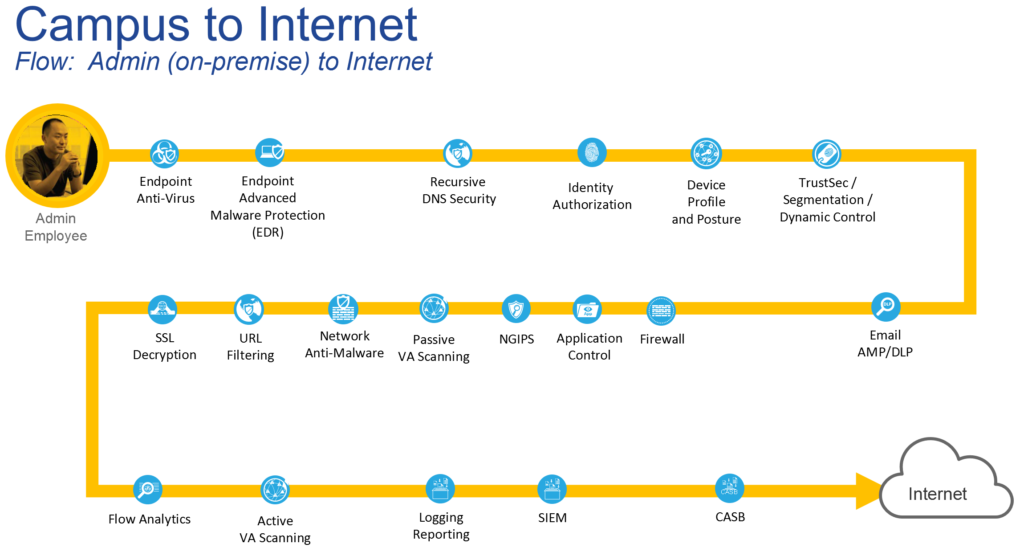
Through dialog, we highlight what capability is currently addressed (technology you own), capability partially addressed (technology you own but have not deployed), and capability not addressed – legend below.
This information is then used to highlight the gaps and number of vendors to solve the problem. This is key to understanding how to address the issue but also looks for an opportunity for better integration. As you can see in the image below we have called out technologies that are required but do not fall under the Cisco security product set – why? Well, it is all about securing the flow and ensuring you have a holistic view of what is required and that is with or without Cisco products.
Finally, we build out the overall report which is typically delivered in a couple of weeks after the session. The report contains the details I have highlighted above and a path forward addressing the gaps. We tie this back to the executive drivers and initiatives as well as the threats to the business and build out a priority list of actions which includes ease of deployment (optional quick wins). This provides both IT/OT and executives a storyboard approach to security.
If this is something you would like to explore please reach out to your local Cisco representative or drop me a line. For more information on SAFE check out our website.
