
6 Steps to get ready for Canada’s ‘Breach Disclosure’ regulation going into effect on November 1st, 2018
4 min read
You may have heard by now that new rules in the Canadian Digital Privacy Act (PIPEDA) are going into effect as of November 1st 2018. Among those rules is the new mandatory notification of any data breach. Organizations will need to promptly notify the affected individuals, third parties, as well as, the Privacy Commissioner of a data breach that can harm any individual known as ‘significant harm’ that includes bodily harm, reputation, humiliation, financial loss etc. A summary of the key changes to PIPEDA can be found here.
These new rules are important because our data is valuable to cybercriminals and they will be relentless in trying to infiltrate our networks. Cybercriminals are constantly evolving their techniques of attack at a much faster pace than defenders. The malware they use is designed to evade detection and as a defender, our ability to protect our organization and recover from a breach will be largely dependent on the steps taken to strengthen our security posture. Prevention is our key objective but a solid Remediation plan is equally important in the event of a breach.
PREVENTION:
1. THE BASICS: We need to get much better at dealing with the basics of cyber security. Patch your applications, operating systems and appliances, make sure you follow your corporate policies around patch management and if needed update your procedures. A great example is described in Cisco’s Annual Cybersecurity report where Microsoft warned about a vulnerability that triggered WannaCry in March 2017 and only after the exploit made the headlines did organizations accelerate their patching activities. Over 2 months elapsed leaving organizations vulnerable to the exploit during that period.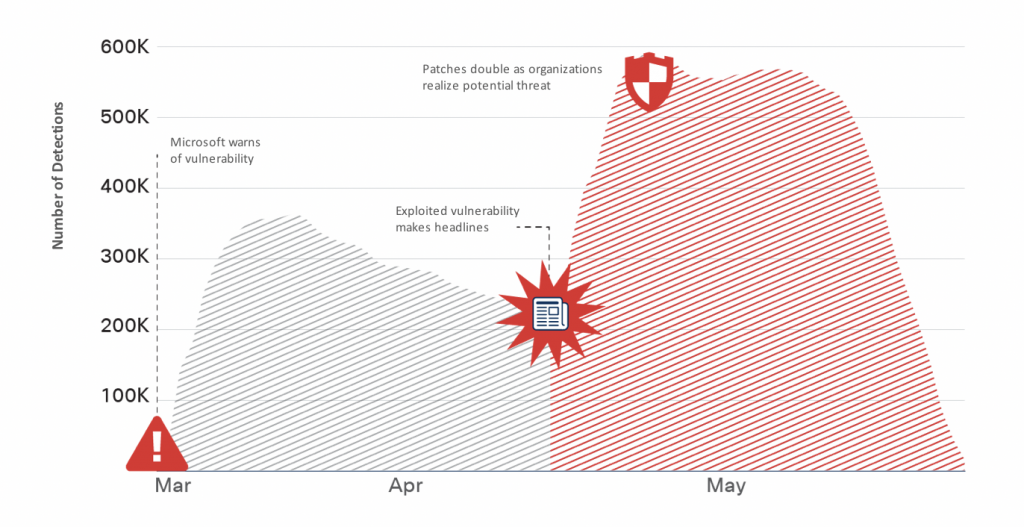 2. THE FIRST LINE OF DEFENSE: Implement a multi-layered security strategy that leverages the internet infrastructure to block malicious destinations. Leverage the cloud to block dangerous connections from being established and stop malware from reaching the network and endpoint. Cisco Umbrella provides a first-line-of-defense with a solution that requires no hardware, no software and can be easily deployed across the entire enterprise in minutes. Powered by Talos threat intelligence, Cisco Umbrella provides protection for users ON and OFF the network and will stop data exfiltration and ransomware encryption.
2. THE FIRST LINE OF DEFENSE: Implement a multi-layered security strategy that leverages the internet infrastructure to block malicious destinations. Leverage the cloud to block dangerous connections from being established and stop malware from reaching the network and endpoint. Cisco Umbrella provides a first-line-of-defense with a solution that requires no hardware, no software and can be easily deployed across the entire enterprise in minutes. Powered by Talos threat intelligence, Cisco Umbrella provides protection for users ON and OFF the network and will stop data exfiltration and ransomware encryption.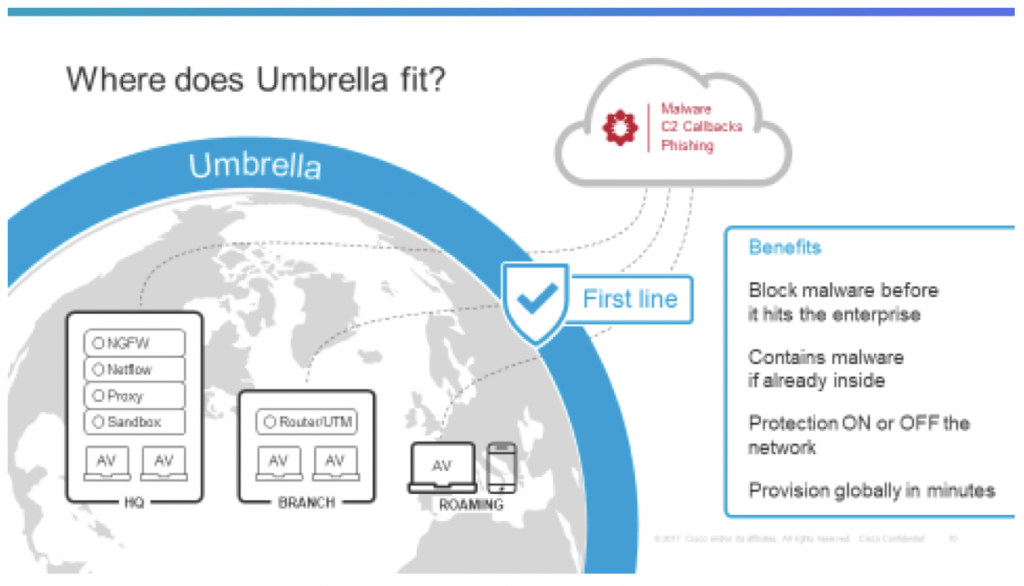
3. NUMBER ONE ATTACK VECTOR: Email continues to be the largest attack vector and the primary tool used by cybercriminals to distribute malware. 90% of breaches start with email because it takes threats directly to the endpoint. The attackers will use social engineering techniques combined with phishing, malicious links and attachments to deliver exploits to the endpoint. Having a ‘good enough’ email security solution is no longer good enough for defending your organization. Cisco’s offers best in class Email Security, that easily integrates with Microsoft Office 365 to provide customers with exceptional threat protection. Cisco’s Email Security solution is powered by Talos threat intelligence.
4. LAST LINE OF DEFENSE: If everything else fails, then your endpoint solution needs to provide protection against the threats; however, you cannot rely on your traditional anti-virus technology, advanced threats will go undetected and can be present in your network for months. Almost all endpoint security vendors claim to block 99% of malware, but what about the 1% that’s missed? The threats in that 1% is what we need to be concerned with, those are advanced and targeted threats that will evade front-line defenses, cause serious damage and steal valuable data. Click to uncover the 1% you care about.
Organizations need a Next Generation Endpoint Security that integrates Prevention, Detection and Response capability in a single solution. Cisco’s AMP for Endpoint is the last line of defense that continuously monitors and analyses files in your network to uncover the 1% of threats that other solutions miss. If a file that appeared clean upon initial inspection suddenly exhibits malicious behavior, AMP for Endpoint will detect the change, contain and remediate the threat and will include a full history of the file activity for forensic purposes.
REMEDIATION:
Are you ready in the event of a breach? Did you know that 60% of breaches have data exfiltrated in the first 24 hours. What is the plan? Pull the network cable to the internet to stop threats from spreading. Cisco Security Advisory Services can help with Incident Response Services.
1. READINESS: Proactive Services include several activities to make sure you are ready in the event of a breach. We evaluate a number of data points to obtain a deep understanding of your environment and your practices. We will coordinate and perform threat hunting work with your team to look for vulnerabilities, malware and active compromises in your environment. We act as a 3rd party in table top exercises to evaluate the effectiveness of your existing Incident Response plan. Based on our findings, we will prioritize our recommendations and will assist in preparing the environment to better prevent, detect and respond to future incidents. Review Incident Response Readiness & Retainer at-a-glance.
2. RETAINER: Reactive Services are needed when you have an inevitable security incident. The Cisco team goes into action within 4 hours and will be onsite with 24 hours of the incident report. The team will assess the situation and initiate a response; they will co-ordinate status, action items and provide updates as needed. The team will do a deep investigation to understand the scope of the attack, deploy the necessary tools to perform forensics and quarantine the attack. Once contained, the team will remove all malware and tools left behind by the attackers. If needed we will bring in our crisis communications team to manage any external breach communication. Review Incident Response e-book.
Take action today:
14 day Trial of Cisco Umbrella
Speak to your account manager about the Ransomware Defense Bundle.