
What I’ve set out to do here is present a methodology that you could use to sell security to an unreceptive audience. This involves taking the CEO and CSO through a couple of short exercises to let them experience exactly what it’s like to have the company they work for, or their home network, breached. The idea is to bring home to them the feeling of powerlessness to be able to do anything to restore things as they were.
It takes years to develop a company’s business processes to any great level. A Cryptolocker breach brings this permanently to a halt, within minutes!
The objective then in a security presentation is not just to engender trust, and 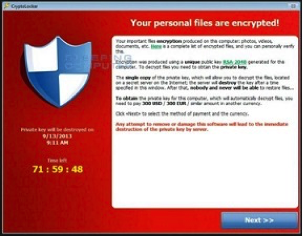 credibility with your audience, but let them experience the feeling of loss that their company will have after a security breach.
credibility with your audience, but let them experience the feeling of loss that their company will have after a security breach.
To begin with your presentation should match the audience’s decision making level. If the CSOs are not in the room, then you should be looking for a champion who will take your message further afield. You need to establish who, if anybody, manages the Cyber Risk.
If none of these criteria are achieved you may as well pack up and return another day, unless you’re known for being able to sell ice to Eskimos. You might also be in the room with corporate employees who are really only interested in determining a level of Risk factor, namely, how a Cyber-attack could affect their company’s share price, and if 10% of the IT budget is about right to spend annually on diminishing the network security risk to an acceptable risk tolerance.
Selling security today is not about selling a bunch of products to your customer. It’s about selling partnership between their company and yours. Network security complexity has far outpaced the skills of regular corporate employees. Security personnel have to change their role to become advisors to their board, administrators of the implementation teams, negotiators with their own departments and their suppliers, and bringing 3rd party security vendors in to test for vulnerabilities in the network perimeter and the workstations – absolutely no  longer the technical role we once knew.
longer the technical role we once knew.
This partnership sale for network security needs also to be a service-centric sale with close cooperation and commitment from the vendor company. The majority of this will be in the digital updates from the vendor’s security intelligence feeds, e.g. Cisco Talos.
So, let’s begin with two short exercises you might try with your audience, remembering that people love stories.
Exercise one
Get your audience to close their laptops, and place these on the floor at their feet. All they have on their desktop in front of them is their mobile phone and a pen. Now switch off the room lights and say “your company has been hit with a Cyber Attack and you’ve lost everything”. “How are you going to recover the business processes?” “You don’t have any IT at all, and no phones except your own mobiles, what are you going to do?” “Where do you start?”
Typically, no one will answer, so wait a few seconds and say then this is where Sony Pictures were a few years ago. They lost EVERYTHING, they had nothing left, no email, no desktops, no desk phones, no future business plans, no movie assets, and no backups – all wiped. This included all the isolated islands of personal data held on individual PCs and laptops.
Say: “Could your company cope with no income for 24 days?” “How are you going to work at what you usually do?”
This is happening to dozens of small business every day, and hardly ever mentioned in the press.
Exercise two
Get each member of the audience to place a credit card into a basket you’re holding.
Tell them you’re only going to keep these for 30 seconds.
Now instruct each member to recall his pin number in their minds to get their cards back.
You say: “Ready?”. “I’ve had your card for 30 seconds, I recorded your card-number and pin. I’ve made thousands of copies of each card and I’m selling them for 50p each down at the market. I’ve made thousands of pounds and no one can track my fraud.”
That’s what happened when you shopped at Target Stores two years ago.
Target Stores had no idea this had happened. It took months to discover, and it was not even Target Stores themselves that discovered the fraud!
Some companies believe that Industry Compliance such as PCI is sufficient security. Regulated public companies do have to comply with specific Regulatory Compliance commitments. I could name several companies that have been breached believing that compliance and security are the same thing.
Many companies are reluctant to invest in sufficient Network security, but this changes when a breach occurs and the wallets open … but only until confidence is restored, then they close again. I have seen many security products in their boxes, and never opened or installed!
Have you heard this question? “What is the least I can do to protect our network?”
The truth is that network security is a cost of sales and must be factored in when moving to a Digital Business Model. Cloud based applications and data brings more things to track since data bases access and data loss can no longer be tracked directly from the corporation’s premises. A cloud based monitoring solution also needs to be chosen to manage the user’s data access.
Here are some givens that the customer needs to put in place before he buys your security products.
If the customer regards your security products as the last stop, he is mistaken.
This is a good suggestion if we accept that “every company will be attacked”.
Besides security what do we need?
Firstly, offline or ‘historic’ backups, and also when in recovery mode, back up the backup first!
I was dismayed last week. A small business was hacked with Cryptolocker, and by the time it was discovered the automated backup sync-process on the servers had backed up the cryptolocked files into the Cloud Storage, overwriting even the Cloud based backups. The customer was not happy when they discovered this!
Over the years I’ve seen that rarely-tested data-base restores go wrong, time and time again!
Create or rent an off-site disaster recovery premises with workstations, phones and a minimalistic infrastructure to continue business. This would be much like a military bunker – tested periodically, includes last week’s data – emails – forums – with personal data in the Cloud.
 If that can’t be afforded, a Cyber war-room would be useful, so long as it does not share any network resources and is isolated completely from ‘Corporate’.
If that can’t be afforded, a Cyber war-room would be useful, so long as it does not share any network resources and is isolated completely from ‘Corporate’.
Pen testing! Test everything. It’s part of any security sale. The majority of successful intrusions, internal and external, are inadvertently the result of user errors. Invite Portcullis in. Engage a company like BitSight Inc. and score or rate your business security defences in comparisons with other corporations operating in the same market space.
I can’t stress Defence in Depth, enough.
The security solution you sell to your customer may become a bandage for the underlying lack of segmentation or defence-in-depth.
A risky sale would be to sell security to your customer if there are none of the following in place:
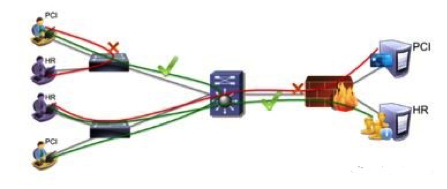
Segmentation of the network, segmentation of the data centre, multiple user rolls, and segmented digital business assets. It’s inexpensive to implement, and the vital first basic network security principal. It reduces the attack surface, is a lot of work to implement, but a lot easier to manage proper segmentation with today’s tools, e.g. the Cisco ISE.
Typical defence-in-depth security layers at a corporation:
Desktop business Antivirus from ESET – includes effective host intrusion
prevention.
- VPN from Cisco – Any-connect 4.1 with the newly added security
 features.
features. - Network next gen IPS security for Perimeter and Data Centre, with Cisco FirePOWER
- Analytic Engines, the very latest way to detect breaches in the internal network, e.g. Cisco StealthWatch (usually for larger companies)
- Cloud Security from CloudLock to track user data base use, users, Apps, and DLP.
- Roaming laptop and tablet client protection using Cisco CWS.
Its recommended that all 3rd party suppliers’ security is also rated by a company like BitSight Inc. so that your 3rd party suppliers enforce your level network security standards before they connect to your applications.
Of course the one thing I’ve not included so far is the corporations’ staff, their departmental leaders, and on the job training. This is ultimately what makes a difference and needs to be in place.
Corporate Security is just hanging on the thread of user security training. Sell this upfront. I am convinced that a little corporate user security training is far better than the often implementing corporate phishing traps I see.
Users need to understand how with just one click, or losing one username/password, can bring down their whole corporation because human error is responsible for the majority of attacks on corporations, and these begin from a compromised end points.