
Why security architecture should always be driven by business need
Last time, I discussed the flaws and limitations of a checklist approach to security architecture, compared with SABSA’s Business Attributes-based approach. This method not only leaves no stone unturned in terms of identifying business problems and assessing your business requirements, but it also translates them into a cohesive, viable and effective security approach. Here’s a reminder of the Enterprise Security Architecture Model I referred to before.
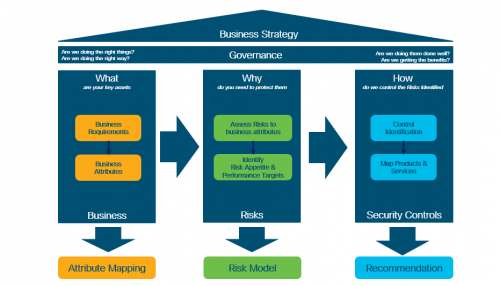
This simple methodology consists of a series of phases that provide an overview rather than a complete risk model. As I said last time, this is called attribute mapping, and helps identify:
What are your key assets that need protecting? This could include both tangible and intangible items, from your brand to IP, strategic partnerships, etc. identification of these assets allows us to build a lite-touch Risk model to establish:
Why do you need to protect these items and what do they need protection from?
How can you achieve this? i.e. which security controls (products, services, solutions) can minimise or mitigate risks.
Business-driven security
This approach exemplifies a business-driven security approach that is both risk-based and impact-based, and it works because:
- It helps you build a security strategy: this is a typical top-down approach that will help map your business priorities to security solutions.
- It justifies your security spend: this is a bottom-up approach that will map back the technologies you buy with your business strategy, goals and mission
- Importantly, it also helps you unlock the security budget:
“We do not have the budget to spend on security.“
Sound familiar?
An issue commonly faced across all areas of business, private and public sector alike, the approaches we’ve outlined can be used to demonstrate to your board why your organisation needs to invest in security, including writing a business case and/or presenting your strategy to the board for your CISO.
From a Cisco perspective, we are committed to helping our customers develop the above methodology. In doing so, we aim to deliver the security infrastructure and service management solutions that genuinely support your critical business initiatives.
A real example in action
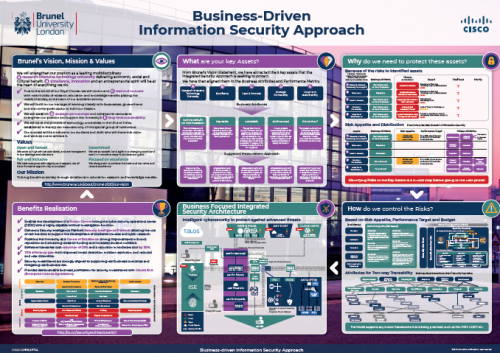
The following image depicts each step of this approach, outlining:
- The customer vision, mission and values.
- Their key assets, which are informed by point step.
- Why it’s so essential that those assets are fully protected.
- How we can work with customers to minimise risk.
- What components are required for a robust, business-focused integrated security. architecture, to help you achieve your business goals.
- Business realisation: the value derived from this six-step process.
Going full circle
Time to look back at our original question and understand why the answer should always encompass each individual customer’s business drivers, goals and objectives, which in turn, must be translatable into business language.
Let’s end by returning to the beginning – and replace that flawed approach with our response:
Customer: “We are launching a new product in our portfolio, and we need to sell more of that product.”
Cisco: “In order to sell more product, your business security should enhance your core offering by 1) ensuring higher levels of trust and 2) supporting ease of use.”
Why?
Because helping our customers grow their business is what we’re about.
To find out more about our security products and solutions, visit our website or contact me.