
Five years ago, one customer asked me for a system that was capable to put up and running the IP devices of their mobile backhaul network and that needed minimal intervention from field engineers (ideally no intervention)
Initially, we though that one of the Cisco Zero Touch Deployment (ZTD) solutions would be a good fit, however once we started to go deeper in the design it was clear that we had some gaps and that we will need a lot customisations. Then a System Engineer from the Account Team highlighted the obvious; if we have to do heavy customisations then why do not explore the systems that the customer already had in production? This customer was already using Prime Network, a Network Management System that once it is able to reach the device via an IP address permit to make configurations and managing the device. And that was the weak point of the solution. We could use a temporary pool of IP addresses allocated to the devices of the edge of the network (Provider Edge, PE) or open a VLAN across the network to a DHCP system or other different approaches but at the end, independently of the solution, we still need to do some device staging, assign an IP address, involve an operator on the Network Operation Center to supervise the process and install additional security elements to control rogue devices trying to connect to the network.
We implemented the solution and together with good processes we were able to meet many of the customer expectations.
If you are interested in some additional details, this was discussed in one of the London CiscoLive session.
Just a few weeks ago I meet another customer that was asking something similar and this time I did not had to reinvent the wheel.
Over the last four years Cisco has put a big effort in a solution that allows discovering and reaching the devices in a secure way and completely routing independent. This solution is called Autonomic Networking.
The aim of Autonomic Networking is to create secure self-managing networks. In a self-managing autonomic system, network management takes on a new role: instead of controlling the network elements individually and directly, the administrator defines network-wide policies and rules that guide the self-management process.
Now let see from a high level point of view how Autonomic Networking works.
It is necessary a Secure Unique ID (this is already coming embedded on the hardware ) that fully identify that device and a whitelist that it is managed in a central element called the Registrar (we could have several Registrars on the network, all with the same configuration), the new devices are checked against the whitelist and if they are confirmed as part of the domain
) that fully identify that device and a whitelist that it is managed in a central element called the Registrar (we could have several Registrars on the network, all with the same configuration), the new devices are checked against the whitelist and if they are confirmed as part of the domain
they will perform a Secure Domain Certificate Enrolment. Only those devices accepted on the secure domain will receive their certificate.
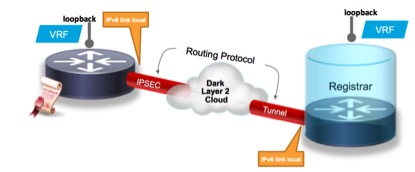
Autonomic Networking uses the Autonomic Control Plane to allows the Self-forming of the network infrastructure domain. It takes advantage of IPv6 Link local in order to provide connectivity between devices and follows the network topology in order to discover all the devices.
A loopback IP address it is generated based in the SUID and a VRF it is created in each of the devices to create a L3 VPN that extent throughout all the devices of the network. This allows to have a Virtual Out of Band Channel that it is not part of the device configuration.
And if we attach a server to the L3 VPN in a similar way like we would do it in a MPLS network with the “ip vrf forwarding” command, this server could connect with any network device via SSH, SNMP, etc using their loopbacks. If for example I connect an Identity Server, like Cisco ISE, the autonomic devices will discover the service and will use the AAA capabilities of ISE. If we attach a TFTP server, it will be discovered and the network can use it as a configuration server to provide the final configuration to all the devices, because until this point, only the certificates are part of the configuration.
Summarising:
The network is completely self-managed with no need of configuration running on the devices. It is secure, with a separate and encrypted VPN. It does not need a routing protocol as only depends on IPv6 link local addresses.
As a final comment it is important to understand that the use of this kind of self-managed networks will require changes in the way we operate the networks. The Operations processes will need to be adjusted in order to take fully advantage.
If you want to get some additional information refer to the following links:
- A Framework for Autonomic Networking
http://ietf.org/html/draft-behringer-autonomic-network-framework - Autonomic Networking: Definitions and Design Goals
http://ietf.org/html/draft-irtf-nmrg-autonomic-network-definitions
1 Comments
If this really works it will be a major step forward in the network automation. Well done Cisco!!