
Stop the spread of malware with Cisco´s integrated security and your window to the magic, Cisco Threat Response
Malware infections are one of the top concerns for organizations around the world. The rapid transmission of these infections can cripple an environment in a matter of minutes, so it is vital to an organization’s survival that they can quickly detect and respond to this type of threat. Companies need to be able to respond to threats with blazing speed, but disparate products make it difficult to rally a timely and effective response.
Fortunately, there’s Cisco Threat Response to bring all the pieces together and deliver better protection. Threat Response is an integration hub marrying global threat intelligence from different sources with local threat intelligence created by your own security solutions.
When you own a Cisco security product, you gain more than cutting-edge technology. You’re harnessing the cumulative power of Cisco’s security community, and the integration that Threat Response delivers helps bring all the pieces together. With one dashboard you have full visibility and enforcement capabilities, integrated out-of-the-box.
One of the most important integrations in Threat Response is for Cisco AMP for Endpoints. AMP for Endpoints is a Next Generation Endpoint Security platform that integrates prevention, detection, and response capabilities in a single solution, leveraging the power of cloud-based analytics.
The Threat Response integration with Cisco AMP for Endpoints helps organizations uncover threats faster and improves overall security effectiveness by combining AMP for Endpoints advanced malware detection capabilities with Threat Response´s visibility of the attack chain and incident response power, to quickly detect and respond to a malware incident before it has a chance to spread throughout an environment.
The Challenge
Malware attacks have grown exponentially over the last decade and are one of the costliest attack types of today. On average a successful malware or web-based attack has cost companies nearly $3.86 million in remediation spending. Unfortunately, this number has the opportunity to skyrocket in the coming years.
This attack type has such a high success rate due to the sophistication used in its delivery and obfuscation techniques. Oftentimes, malware infections go undetected for long periods of time which allows it to rapidly spread throughout an environment causing the maximum amount of damage.
As a result, organizations and security managers are often left asking themselves a number of questions, including but not limited to:
- How can my organization protect itself from the costly attack types targeting our business?
- When a new threat is discovered, how can I know if we are affected?
- How can we gain full visibility of our endpoint activity?
- How can we quickly uncover malware threats and strengthen our overall security posture?
The Cisco integrated security solution
The integration between Threat Response and AMP for Endpoints presents organizations with full endpoint visibility and swift response power to allow their network defenders to stay ahead of their adversaries and improve their overall security posture. Equipped with AMP for Endpoints´ advanced threat detection capabilities and Threat Response´s integration with other Cisco security solutions like Umbrella DNS security, Cloud Email Security, Firepower devices, organization’s mean time to detect previously known and unknown threats is greatly improved. Time to remediation is accelerated, which provides incident responders the tools necessary to quickly uncover and eliminate threats to their environment and reduce overall dwell times experienced with these types of attacks.
Use Case
Now let’s look at two simple use cases in action.
Phishing campaign
A new phishing campaign has been launched against your industry and you obtain threat intelligence from the National Security Agency, your vertical´s CERT, or a Cybersecurity blog from the likes of Cisco Talos.
For an Incident Responder, the first question asked is often; Are we affected? With the external threat intelligence ingested by Threat Response, the Incident Responders will immediately have at their fingertips the verdicts of the Indication of Compromises (IOC) fed to it, combined with potential affected internal computers. All in a contextual, intuitive and interactive visualization view, ready for drill-down to the individual endpoints for deeper investigation or direct remediation from Threat Response. If the company´s infrastructure is not affected, preventive measures can be done from Threat Response to block a future attack.
On the other hand, if the company has an affected machine, current and historical activity, whether any other machines have interacted with the malicious file, can be exposed and the attack remediated. With full insight into attack processes in the endpoints.
If the customer uses other Cisco security tools, Threat Response can provide a full view and insight into the complete attack chain.
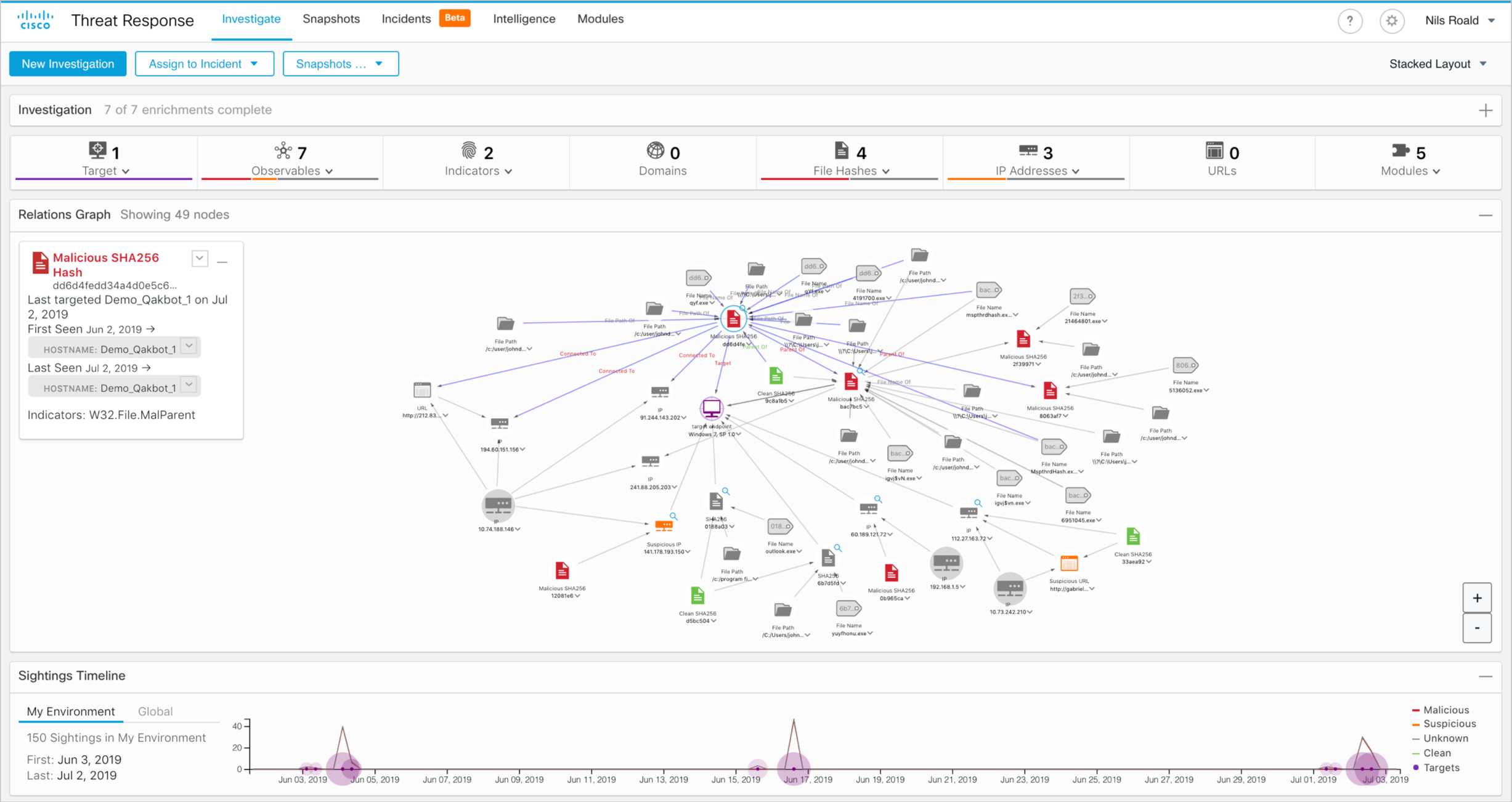
In this Threat Response investigation, the customer has deployed Umbrella DNS security, Threat Grid Cloud and AMP for Endpoints. The out-of-the-box integration between these Cisco security solutions and Threat Response provides an instant view to IOCs for a malware campaign and their potential effect on the customer´s endpoints. In this event the company has one affected machine, which is compromised by multiple malicious files, connected to suspicious IP-addresses and delivered by Outlook. Typical for a phishing attack.
Suspicious file
Suspicious activities can be discovered in a single internal computer. After assessing the maliciousness of the file an Incident Responder ´s next questions to answer is often; Has this file spread to other machines and how did it get into our network? To investigate an unknown suspicious file in the customer´s environment, Threat Response is perfect to disclose if there has been a lateral movement to other computers and how the file entered the corporate network.
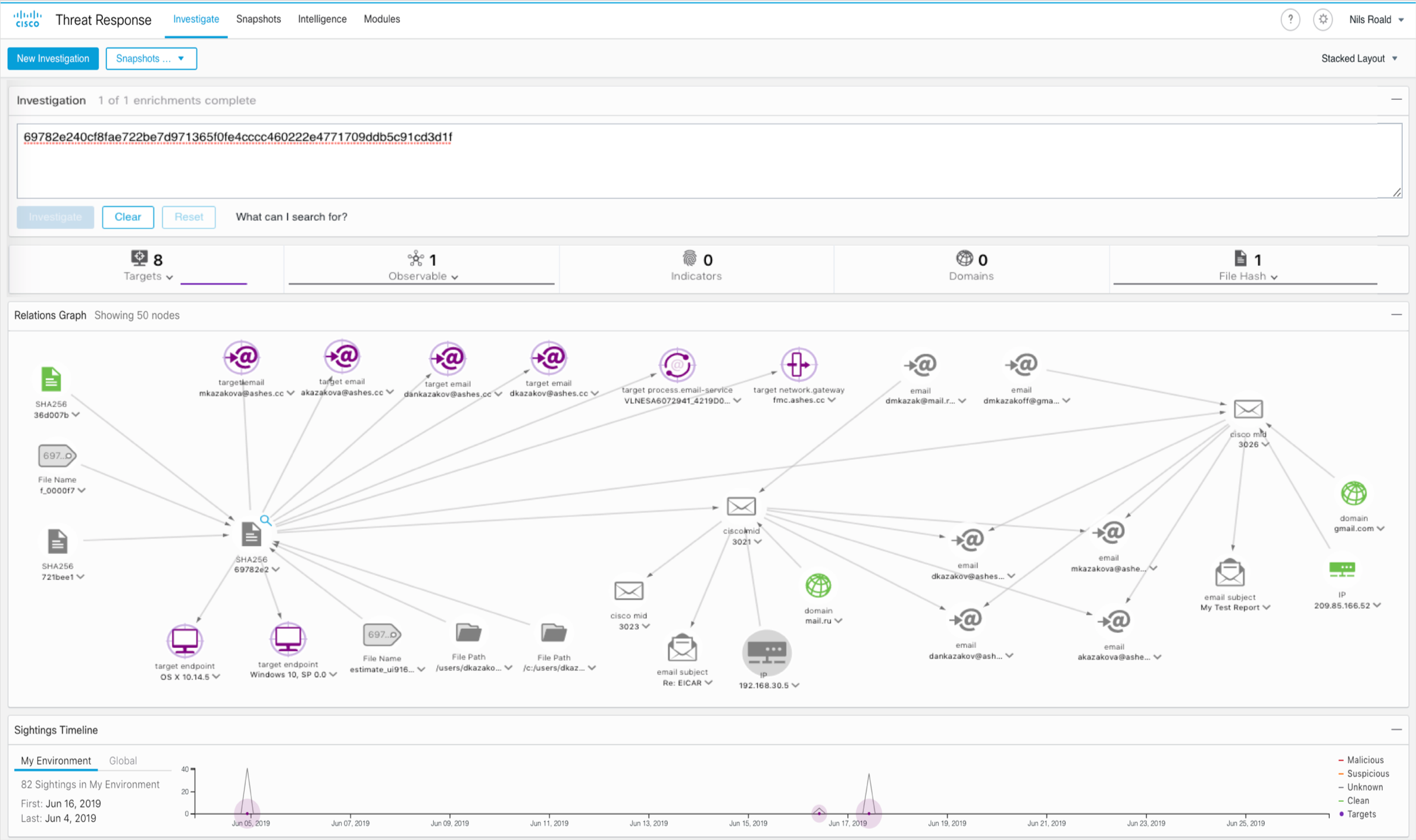
In this Threat Response investigation the customer has deployed Firepower firewalls, Cloud Email Security, Umbrella DNS security and AMP for Endpoints. The out-of-the-box integration between these Cisco security products and Threat Response provides an instant view to the attack chain from the network through to the endpoints.
Here we see the suspicious file has been delivered via two individual emails passing through the corporate firewall and email gateway. From two well-known public domains; gmail.com and mail.ru. The attached file is sent to four different mailboxes, but with two different email subjects. Conclusively, we see that two recipients already have the suspicious file delivered to their computers.
Summary
By combining the power of Threat Response, AMP for Endpoints and other Cisco security solutions, it enables organizations to stop malware in its tracks through full visibility, threat hunting and remediation capabilities. Security teams can quickly uncover threats, improving the organization’s overall security posture, while ensuring full endpoint visibility.
To lower the Time-to-Protect and Time-to-Detect have always been the center of attention for the cybersecurity industry and its customers. A third term, Time-to-Integrate becomes more and more imperative due to fragmented and isolated security solutions addressing multiple different threat vectors. Out-of-the-box integrations to provide full visibility to the attack chain and enforcement capabilities are the key to a successful defense against modern cyber threats.
If you would like to learn more about Cisco Threat Response, check out our on-demand webinar: “Stop threats quickly by integrating your Cisco Security products”.
Tags:


