
Malware is a reality
Fifteen, maybe ten years ago, the world was still quite simple: a few Layer 3 rules were configured on the firewall to restrict connections to services and/or IP addresses. Today such simple rules are by far not enough anymore: payload and malicious software have long since learned to overcome NAT using hole punching and tunneling traffic over other protocols (such as HTTP). They use that and countless other techniques to hide malware in otherwise harmless files in order to outsmart the combined intelligence of firewalls, virus scanners, sandboxes and others.
The old “setup-and-forget”-approach of the past gives you nowadays only a hopelessly deceptive (and often negligent) security. Against today’s sophisticated attacks such as WannaCry, which spread over millions of devices within a few hours, you have only a chance by using current device firmware and automatically updated signatures. Take a look at the Cisco Security Report, where we explain in detail what the reality about security today is.
Cisco Talos and Meraki: Safety in no time
Fortunately, the 600 security researchers at Cisco Talos cannot only write impressive reports. Above all they provide 24/7 security information, in the form of so-called signature updates. These get distributed to millions of Cisco products within minutes to be used for filtering traffic. This does also benefit the Meraki MX Security Appliances, which do receive the same signature updates as other Cisco products, namely the Snort IPS / IDS Engine and Advanced Malware Protection (AMP). The beauty of the Meraki solution is: You don’t need to be afraid of the configuration! Four clicks to activate enough, the rest we take over for you!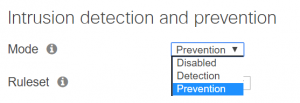
Better late than never
So far, so good – we have now a state-of-the-art protection for our network.
Unfortunately the state-of-the-art also says, that at today’s breathtaking propagation speed of attacks no solution can guarantee 100% recognition rate – the best in the market (like Cisco) are close, but a small gap always remains. Cisco AMP offers an unique added value in this case:
We continue to check signatures against newly added rule sets even after downloading a file.
So, if a user downloads a file on Monday and on Tuesday it turns out to be malware, you’ll still be better off if you’re notified on Tuesday and can take countermeasures. With Meraki, also this is quickly and easily configured by setting email recipients to be notified about such an event: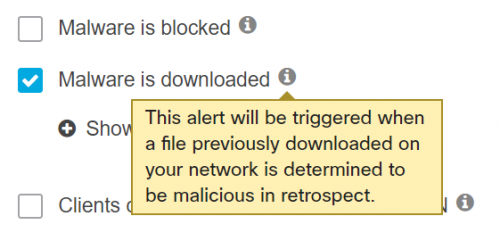
Curious? Let us know , we’ll get back to you and show you how easy it can be to have a secure network!
Disclaimer:
This article is inspired by an article of my colleague David Hopfmüller in the Austrian Cisco Blog.