
Mobile applications allow you to manage nearly every aspect of your life. Would you like to keep track of how many glasses of water you drink in a day? There is an app for that.
Filming and editing an entire movie on your phone? No problem.
What about adjusting the temperature in your home while you are out? There is one for that too.
The concept of the smart home is growing in popularity. Now, you can control almost every appliance and utility in your house remotely with a smart home application. Alexa has moved in with you and listens to your every command. But have you ever asked yourself what these apps are doing in the background? Is your data safe? How can you protect yourself against hackers? Are your applications the enemy within?
From home to office
The digitization we are seeing in our homes is happening in our offices too. Work processes are being automated, transacted electronically, and are becoming more mobile. In turn, this digitisation increases the chances of data leaks and cybercrimes.
In our personal lives we are often negligent with our data by giving applications full access because we do not recognize or understand the risk. Many services know a lot more about us than we think. So how do we ensure that enterprises understand the level of risk posed if we are still struggling with it at a personal level?
Cyber risk is more than a technology or security issue, it is a business risk
There are several examples of cyberattacks where sophisticated hackers compromised confidential data. This includes most of the time emails and plans of some blue-chip clients. In a recent one, according to the press, the administrator’s account has been hacked, which gave the hacker full access to all areas.
Many attacks target mobile apps and operating systems in order to steal sensitive data. Most companies are not prepared to deal with these threats. The more we use smartphones and tablets in the workplace, the more our enterprise mobile apps become high value targets.
The increase in the volume and value of enterprise data is also making companies question how they manage their data centers:
- Are we processing data in line with our company’s compliance and safety guidelines?
- Which security rules are being applied to which applications and data? Are they up to date?
- Where are our applications physically stored and which resources do they consume?
- Who has access to what kind of data?
With cybersecurity, it is not a question of ‘if’ an attack is going to happen but ‘when”. And when it does, which applications will be affected.
Cisco customers are concerned about 3 core areas: Where everything connects, where applications and data are stored, and how everything works together.
Visibility, Segmentation and Threat Protection
If an attack is happening, this is how we protect the data center: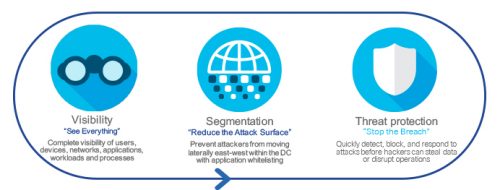
- Visibility: See Everything
- Segmentation: Reduce the Attack Surface
- Threat Protection: Stop the Breach
If you have full visibility of users, devices, networks, applications and workloads in your data center, you are ready to take immediate action when an attack happens. For smaller zones you should keep servers and applications separate from each other and reduce the attack surface. With segmentation into zones, you can prevent attackers using the application whitelisting model. Here, the only traffic permitted between end points is that which meets a policy set by the administrator. Policies describe and define the type of communications permitted between zones or applications. They can be hierarchical for the entire zone or specific to an application.
Last but not least, you need to prevent an attack from becoming a breach. Rapid response to malicious or anomalous activity is essential. With threat protection, you are able to quickly detect, block and respond to attacks before hackers can steal data or disrupt operations.
It is very important for companies of all sizes to have a strong security posture. With the right tools and processes in place, it’s possible to see threats and ensure you have the ability to respond rapidly and in a targeted and effective way.
From a personal perspective, employees also need to be more aware of what type of data we share with third parties. Have a look into our E-Book to learn more about Security in the Datacenter.

