
What security posture should you adopt in order to effectively answer your security incidents?
There is no easy way to say it: Cyber-Security incidents are still one of the most left behind action in today’s company agenda (are often not considered as a top priority) . Lack of visibility combined with low people capacity (a talent shortage) to manage all the deployed point products solutions is not helping moving business towards a threat centric focus (Approach). If the goal is to have a security strategy that is simplified, automated and effective, reality is often different leading in (to) multiple unseen breeches, data loss, long recovery process and generally resulting operation spendings increase. Adding on top of that GDPR, IT budget cut, cloud adoption, IoT and mobility, all increasing the amount of threat vectors in a borderless hacking landscape.
How comes all the cyber-security investment made are not paying off in the threat landscape world? How different is the landscape today? What people and technologies are really needed? In this article we will have a look first at the threat analysis landscape, how do you define a threat centric strategy focused of visibility and relevant data collection? Then we will talk about incident response, what is an incident, how should they be handled and what process and people tasks should be defined for effective response.
Understanding the threat centric world and planning accordingly
Cyber-Security industry is moving towards a multiple vector threat centric attack model, it is important to understand these vectors at first for applying it to your environment. First let’s define threat, according to OWASP a threat is an occurence that can affect a Systems as a whole, while often confused with vulnerabilities. Vulnerability is a flaw that makes a system exposed to an attack or threat. In order to protect your organisation, you need to know what you are protecting, and how you protect it. What are the critical Information Systems asset you want to secure? The idea is to put yourself in the hackers shoes. Once this is identified then you can define the attacking vectors and the threat modelling to put in place. The following are some exemple of threat vectors based on general company’s IT assets:
- Malicious email attachement, or phishing URL in email.
- Compromised mobile device with malware
- Malicious Webpage
- Social engineering conversation through social media to obtain sensitive information
- Personal information leak gathering through a data base with default/no credential
- Router with default settings
- Open port on Firewall
- Cloud application vulnerabilities or default password
- Vulnerable application used by hosts
- Endpoint user with above role privileges
- Poor / no network segmentation
- IoT device with default management addressing scheme
- unprotected/Open API
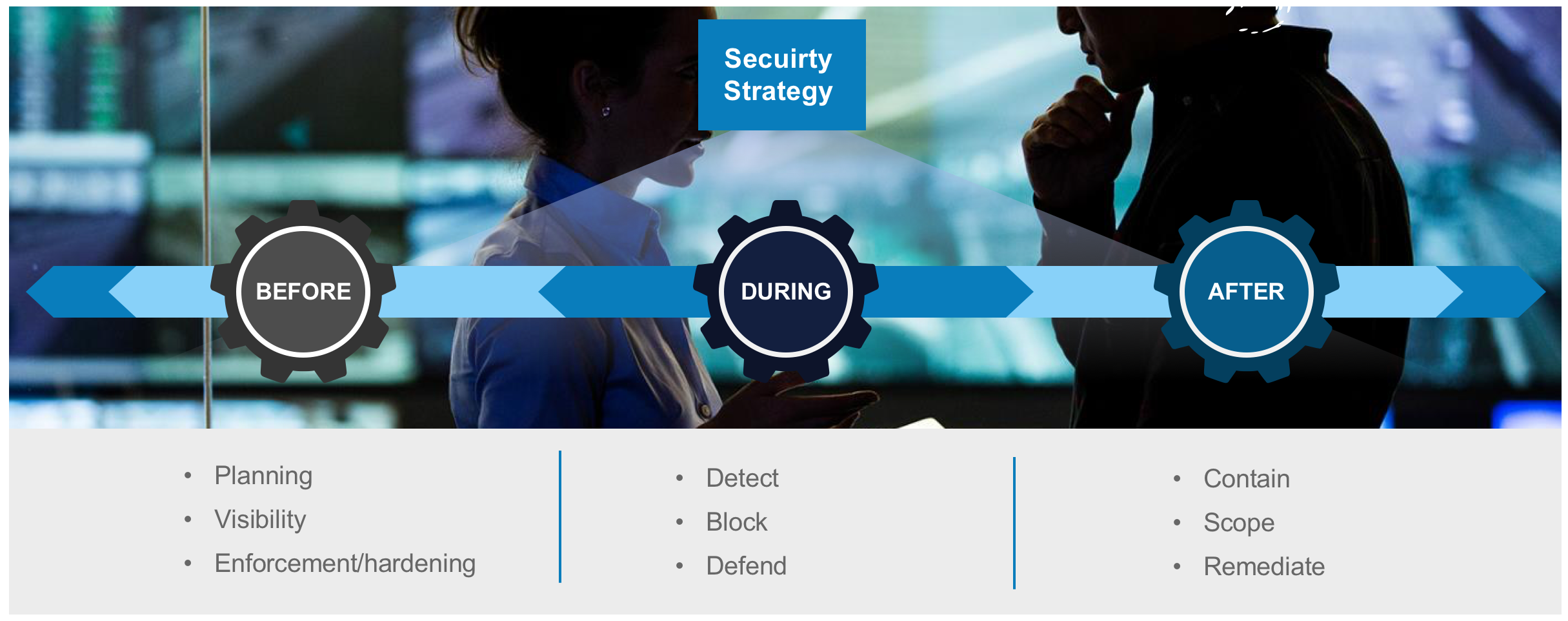
From the above exemple the attack surface has been spread not only at the perimeter but everywhere, meaning that cloud, mobility, IoT should also be considered as part of the security strategy for any given organisation. In order to defined the Security Strategy, you need visibility to plan, define and enforce. Visibility is the key for your organisation as you cannot protect against what you do not see. Let’s assume a security strategy in 3 phases, before and attack, during an attack and after an attack, as explained in the below picture. The main idea to get out of this picture is that it is not possible to have a security posture that will protect you 100% upfront, your organisation is going to get compromised at some point and you need a plan B associated with a continuous approach. This section is going to describe the before phase discussing visibility, planning and collection of relevant data forensic to set the foundation of your security strategy.
In order to be bale view more, there are tools that would be required, and most organisation already have some them in place. In the planning phase, or in the preparation before an attack occurs, there are some solution that a company can leverage to both gain visibility and collect event evidence of security intrusion. Before moving to the gathering of data sets, let’s have a look at the common security elements that can be leverage for the forensic collection phase. Below are exemple of security event that an organisation can leverage.
- IP addresses
- Hostanme and domain name
- URI, URL
- Client and server port indetity
- Process for file or registry modificaiton
- System API calls
- Files hashes (SHA256)
- Behavioural malicious signature
- Exploit based IPS signature
- DNS based resolution logs
The above event exemple, are going now to be described with the different solution set that can be put in place along the different threat vector to be able to leverage the visibility and collection of secuirty forensic data.
Gathering events from the network infrastructure devices: (including cloud services)
The network is the platform where everything transit, again it is a huge asset for your security strategy. Imagine how much information you can collect, from routers, switches, firewall, IPS, email gateway, web proxy, wireless lan controller and many more. All theses sensors are playing a key role for feeding and filling your visibility gaps. Think about it in terms of events, DHCP event, Syslog event, VPN logs, Firewall logs, Netflow and so on. However, keep in mind that these appliances are also leverage by hacker to compromise your infrastructure and manipulate your data, therefore protect your network devices. Cisco for example has several available resources for mastering the security and integrity of your infrastructure.
Below are some exemple of solution you can use for collecting information from the network infrastructure.
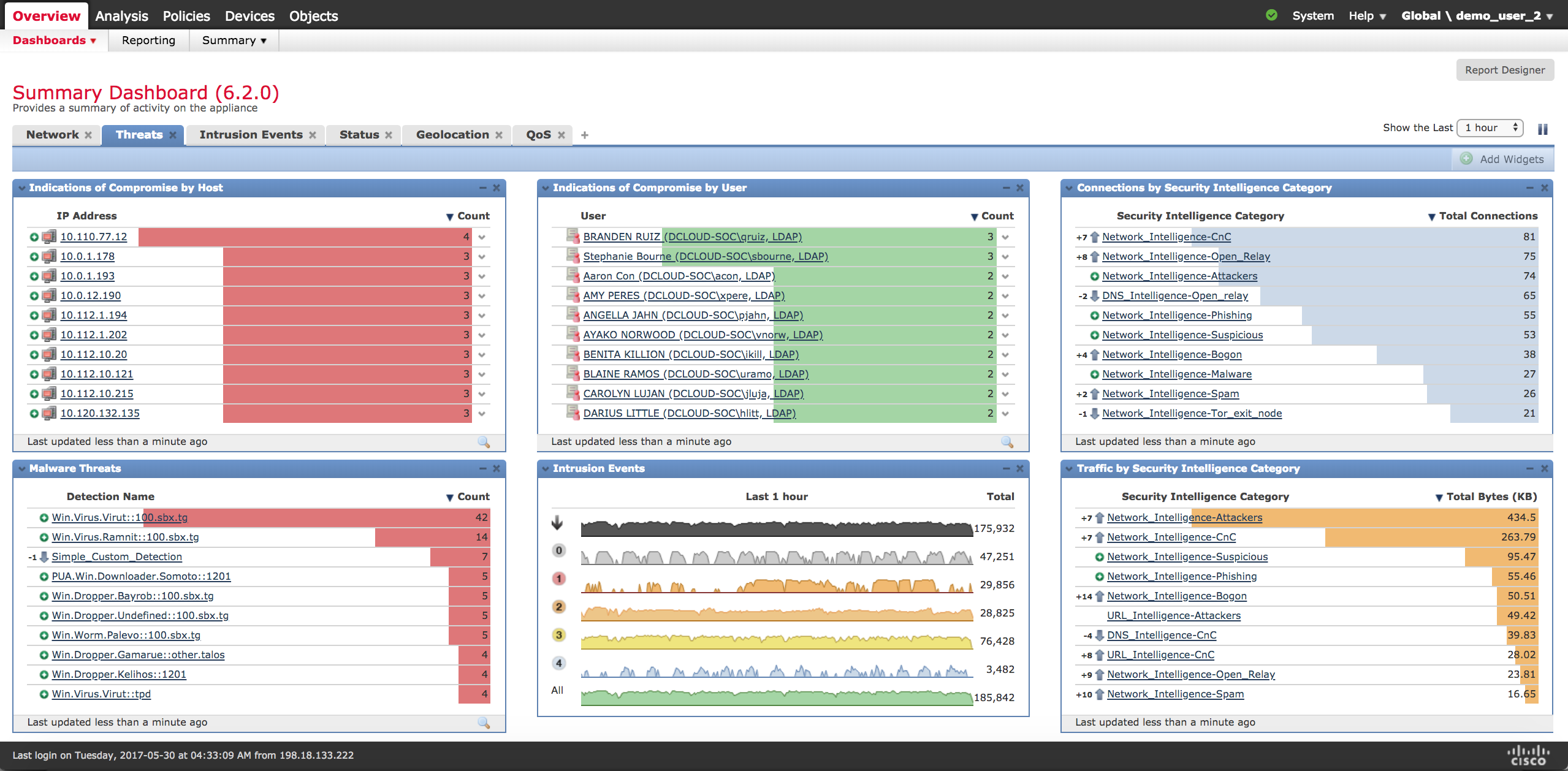
Perimeter security is often the first tool that most company already have, NGFW is generally showing IP address information, hosts information, connection, intrusions events, malware event. The Firepower System is a threat-centric security system aligned with the perimeter needs. It provides security controls using its centralised orchestration including firewall, IPS, and advanced malware protections, while providing enhanced visibility into advanced threats. This display below shows a summary dashboard of threats seen on the company perimeters network.
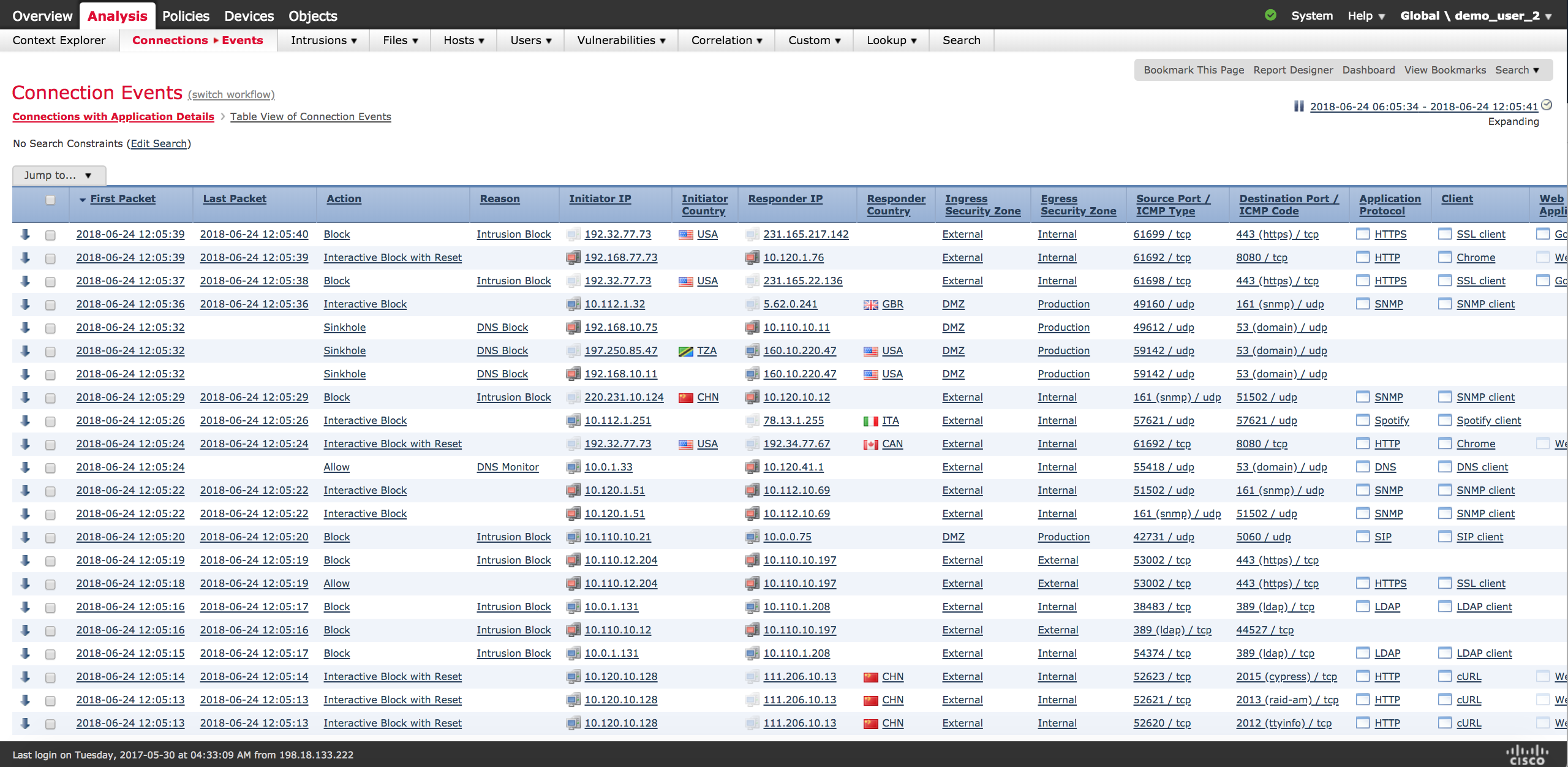
The screenshoot below also show the connection event giving tremendous visibility input displaying various type of event as mentioned in the event type list, this will help increasing visibility into your infrastructure and understanding what goes through your infrastructure both inbound and outbound.
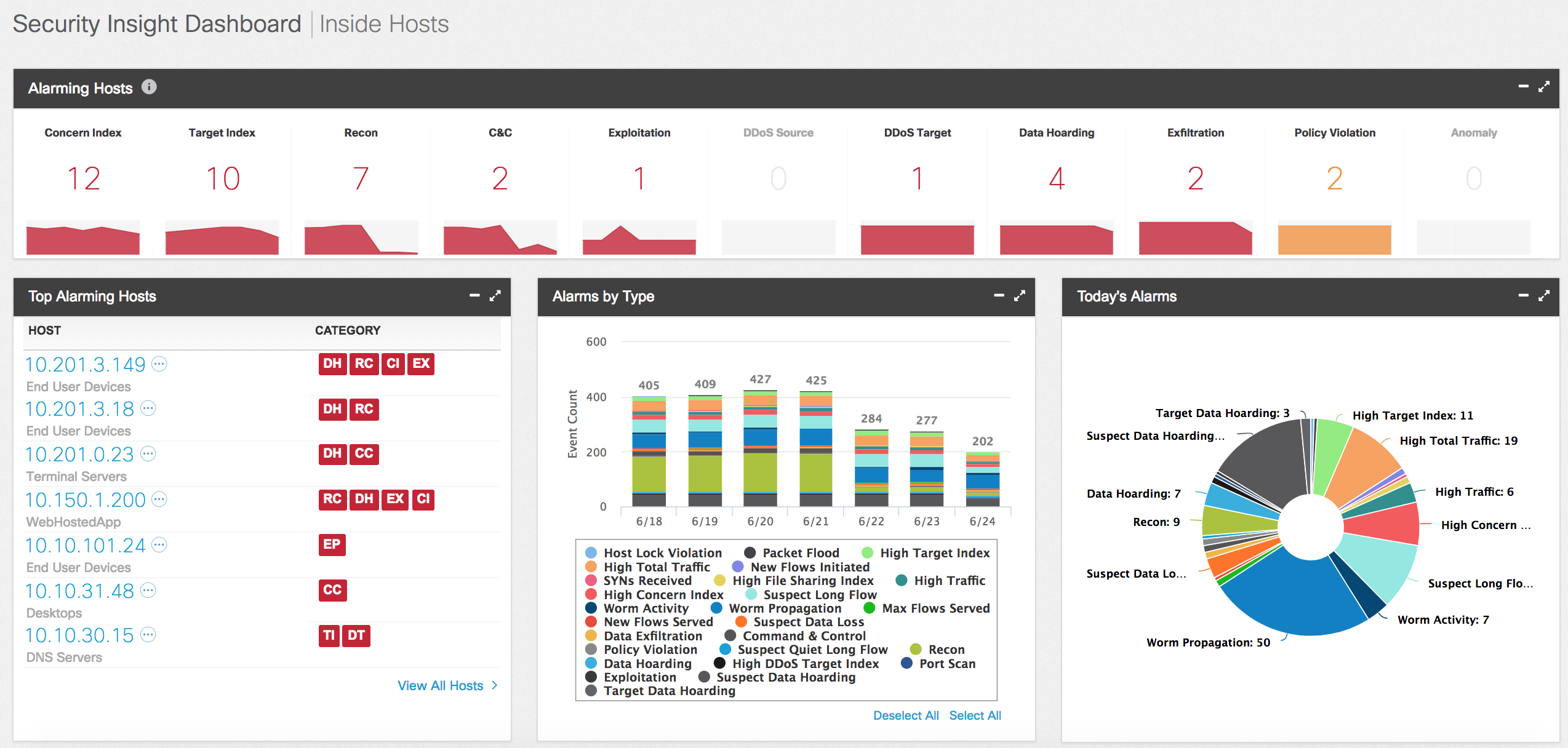
For gathering event from the network, Netflow solution also address visibility chalenges, traditionally network security has relied on perimeter devices (NGFW). One of the limitations of that method is gaining insight into what is happening throughout the network. By enabling NetFlow across all devices in the network and by sending that information to the StealthWatch system, we are able to gain network-wide threat visibility and turn the entire network into a security sensor. The Cisco StealthWatch System provides enhanced visibility into advanced threats by identifying suspicious patterns of traffic within a network. It can also provide visibility into cloud application often being an extension of the permitters. These suspicious patterns are supplemented with contextual information from other Cisco/Non-cisco devices to improve the overall analytics and establish specific threat levels associated with an activity.
For collecting network data, DNS intelligence is also playing an important part of the puzzle when talking about visibility. It is often used by attackers to start malicious Command and Control channel communication. This can also be prevented with Cisco Umbrella, DNS based security cloud services. In the showing below we can see the the DNS activity offering the visibility across the entire organisation regardless of perimeter, mobility and cloud. It can also provide visibility into cloud application like shadow IT, often being seem an extension of the permitters these days for agility purpose.
Gathering events from endpoints, servers and mobile devices:
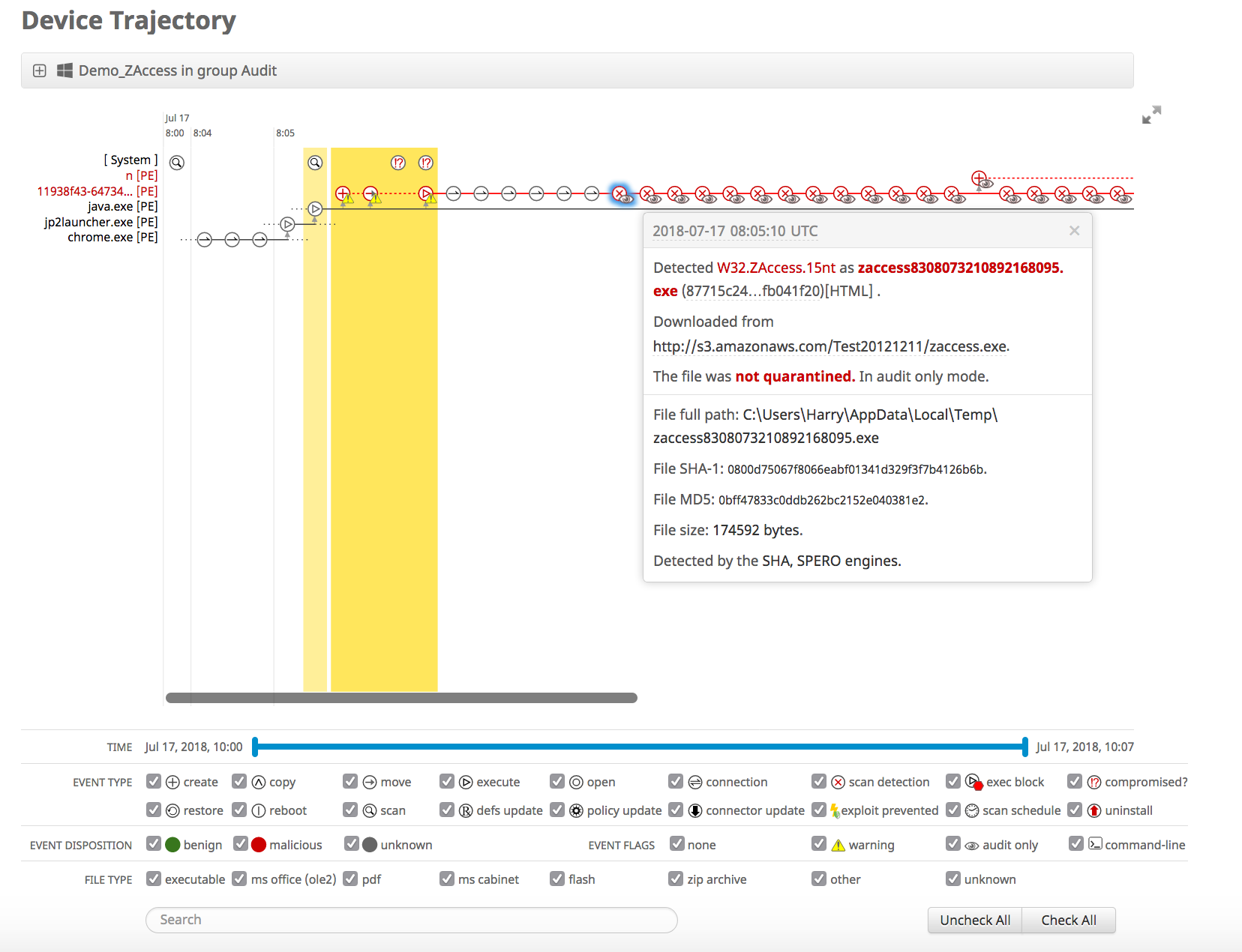
Moving now to the endpoint, this is also key components of the strategy in order to prevent or minimise the contamination of a targeted host or server. Several tools are available from systems disk backup, memory management, OS vendor tools for registry, files system, MDM, Network access control solution, Anti Virus (AV) and Endpoint Detection Response (EDR). In this case for collecting endpoint events we are going to look at an EDR, Cisco Advanced Malware protection (AMP). AMP as discussed on the network collection part above is also an endpoint connector that provides a visibility on the endpoint to a centralised console, giving forensic on event happening on an endpoint. The idea here is to get to know behavioural detection, correlation, indication of compromise as well as a set of actions seen on the endpoint. This tools are very powerful capabilities as they record every transaction and provide retrospective analysis, this retrospective security keep track of the data from what occurred in the past, when a file’s disposition is changed, AMP provides historical analysis of what happened, allowing you to track the incident and infection. This is also what we discussed in the strategy for the after an attack phase, it let you contain and remediate an attack that has occurred in the past but were allowed due to lack of visibility and knowledge about the malware. The figure below, show the AMP for endpoint device trajectory, with the process running on the endpoint on the left, the different action triggering indication of compromise, and below the action taken on the endpoint. This gives also a time scale that permit to go back and forth within the time of the recorded connection.
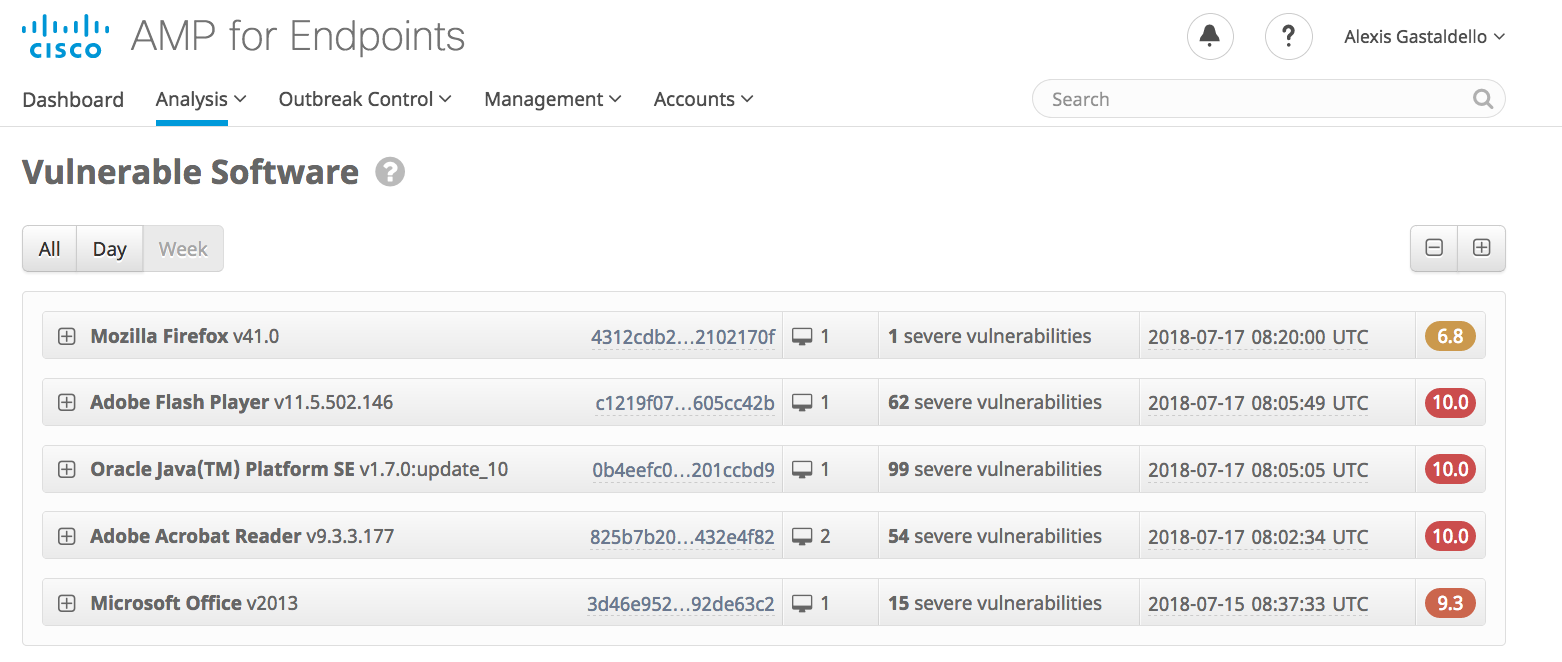
The second screenshoot below is describing the vulnerable software that you might have in your environment, this tool allow you to understand potential weaknesses on your endpoint environment and help you understand critical applications running on the endpoint and prevent future exploits. AMP for Endpoint gives you visibility on the number affected by an Common Vulnerability Scoring System CVSS, provides a way to capture the principal characteristics of a vulnerability and produce a numerical score (O-10) reflecting its severity. In the below capture we see applications and the number of endpoint affected as well as the scoring on the right.
Lastly, for mobile devices, wearables, IOT devices, tablets and unmanaged devices in the same way as the desktops, they also could represent a threat in your environment, therefore it is important not to neglect that vector. A protection mechanism could be solution like DNS based security for instance as these devices relies heavily on DNS to geolocate themselves or to speak with back-end specific infrastructures on the internet. DNS based security constitutes a must for being able to see what undergoing with inside to outside traffic. MDM can also be considered for mobile in order to better managed and see the mobile activities.
To summarise, now that we have an understanding of how you can better understand and see what is happening in your network through many available tools, we are going to see what do to with all the events, alerts and generated incidents from these solutions. How to automate as much as possible, leverage an architecture approach and make you infrastructure smarter as the threats appears in your environments.
Additional Reference:
https://www.owasp.org/index.php/About_The_Open_Web_Application_Security_Project
https://www.owasp.org/index.php/OWASP_Cheat_Sheet_Series