
Let’s Talk Operational Technology (OT) Intent-Based Security
The Internet of Things (IoT) has become what Mufasa is to the Hyenas in The Lion King. It’s a name everyone knows but also fears – and let’s not even talk about deploying.
Yet in practice, IoT wants to help you connect everything you can possibly imagine and provide you with all the data you’ve ever wanted across your extended enterprise.
IoT is your friend: Don’t fear it
With the right infrastructure, IoT will save you time and money: so all in all better TCO and business strategies.
This blog focuses on OT Intent-Based Security, and how Cisco supports this. First of all, we need a few introductions, so please meet:
- IND- Industrial Network Director; a management platform for Industrial Ethernet with many hidden qualities.
- ISE- Identity Services Engine; the policy, profiling and segmentation engine.
- StealthWatch; A visibility and security analytics solution providing advanced threat detection using machine learning and advanced behavioural modelling.
Most of you may have met before, but not together!
ISE and StealthWatch? I thought we were talking about OT
Yes exactly. ISE and StealthWatch can perform the same amazing roles in your OT environment as they do in your IT environment.
How? They reach out to IND who speaks protocols (Industrial languages such as Modbus and Profinet). IND can translate the network language in your OT environment to IT (Information Technology) language. Have a look at the picture below:
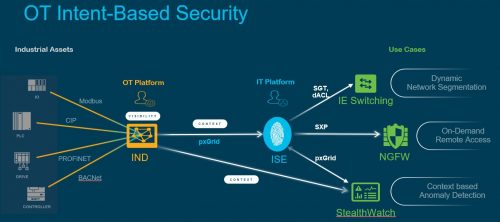
Your Industrial endpoints whether it is a robotic arm, a drone, a traffic light or an I/O speak industrial protocol and this means IT can’t differentiate these endpoints as this is a different language. Due to these linguistic differences we use IND as a translator between OT and IT.
IND understands most Industrial Protocols and can see what endpoints are connected to an Industrial Ethernet switch and will translate this to ISE and StealthWatch.
This means ISE and StealthWatch can see and understand the OT Network to create policies, profiles, understand behaviour, create segmentations and remediate in your OT network.
Yes, you can extend those same capabilities to the OT
So if you ever thought I wish I could:
- Securely segment and set policies in my OT Network
- Have my engineers working remotely to solve technical issues
- Immediately understand when a machine is not being itself
- Merge your OT & IT Networks and departments
Now you know that you can. You can have access, control and visibility of your entire Network, OT & IT. This means a secure, compliant, agile and productive network that is ready for your IoT journey.
Watch the video below to see how it works.
Get more information on expanding IT’s reach to centrally secure IoT endpoints
Tags:- #IND
- #industrialnetworking
- cisco
- extendedenterprise
- intent-based networking
- IoT
- IoT
- ISE
- operational technology
- Stealthwatch



