
Security Tip of the Month: How can we trust the VPN endpoints?
As the Covid-19 pandemic continues spreading across the world, many companies are requiring employees to work remotely from home, putting unpredictable stress on remote networking technologies and causing growing bandwidth demand and security concerns.
VPNs are Virtual Private Networks, they extend a private network across a public network and enable users to send and receive data across shared or public networks as if their computing devices were directly connected to the private network.
VPNs were first developed in the early 1990s, being used only for dial-up connections and to create private networks across public infrastructure, offering access for remote workers in large tech companies. Now the technology is widely available for all types of businesses and consumers.
Remote Access VPN works by connecting users to private networks from a remote location using a laptop, desktop or mobile device using the internet, thus establishing a secure connection remotely. All the VPN traffic is routed via Internet through an encrypted virtual tunnel, creating a secure and private channel.
The data transported by the VPN is secured by strong encryption algorithms and this is the highlight of the VPN technology, but is the data that the VPN tunnel is carrying secure? How we can be sure about it? How can we trust a device that is not in our company and is not daily checked for vulnerability and patched?
As reported by NIST (National Institute of Standards and Technology) some of the most important Remote Access Vulnerabilities are:
- Remote Access client devices generally have weaker protection than standard client devices
- Many devices are not managed by the Enterprise
- No Enterprise firewalls and antivirus
- Lack of physical security controls
- Remote Access client devices may be used in hostile environments but not configured for them
- Exploitation of remote access devices and users
- Phishing, keyloggers, to collect credentials and other sensitive data
Following all the possible vulnerabilities, endpoints might not be compliant with corporate security policy, which can require, for example, a proper Windows patching level or up-to-date antivirus DAT files. In this case, a high possibility exists that the endpoints will forward their infection to the internal network.
The VPN clients can become a source for spreading viruses, worms, network attacks, and Trojan horses into the corporate network.
Cisco offers a valuable solution to this problem with the ISE Posture over AnyConnect Remote Access VPN on FTD (Firepower Threat Defense)
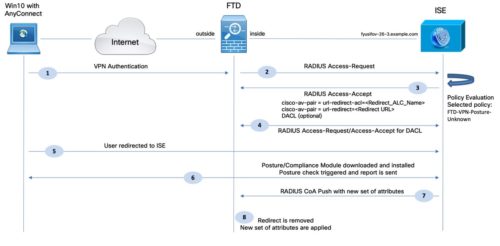
Upon initial connection, the VPN client authenticates to ISE and is matched against a Posture Unknown Authorization Policy (FTD-VPN-Posture-Unknown in the example)
The FTD then redirects web traffic to ISE, where the user is provisioned with AnyConnectPosture Module and Compliance Module.
The agent then performs specific checks on the endpoint in order to determine its compliance against a configured set of posture requirements, such as Operating System (OS), AntiVirus, Patches, Service, Application, or Registry rules. (these conditions are defined by the organization)
Posture requirements are based on a configurable set of one or more conditions. Simple Conditions include a single assessment check. Compound Conditions include a logical grouping of one or more Simple Conditions. Each requirement is associated with a remediation action that assists endpoints to satisfy the requirement.
The results of the posture validation (Compliant or Non-Compliant) are then sent to ISE, that will apply the proper Authorization Policy result. If the machine is deemed “complaint”, then the ISE can send a RADIUS CoA (Change of Authorization) to the FTD with the new set of authorization policies. After successful posture validation and CoA, the user is allowed access to internal resources.
Endpoints deemed “not compliant” with Posture Policy may be optionally quarantined until they become compliant. During this phase, a typical Authorization Policy may limit a user’s network access to only posture and remediation resources. If remediation by the agent or end-user is successful, then the Authorization Policy can grant privileged network access to the user. The policy is often enforced using downloadable ACLs (DACLs) or dynamic VLAN assignment.
Posture is an ISE service that allows you to check the state of all the endpoints that are connecting to a network for compliance with corporate security policies. This allows you to control clients to access protected areas of a network even if they are far from your Enterprise and daily out of your control as the VPN endpoints.
And that’s it! Contact us for more information, we will be happy to help you secure your network.
Tags:1 Comentários




Great content here. Thanks for publishing. We also have an integration we have built out with Cisco to bring Zero Trust Network Access type controls to existing/new Cisco AnyConnect users. More at https://www.ericom.com/ericom-application-isolator/